156-215.80 Exam Question 101
How is communication between different Check Point components secured in R80? As with all questions, select the best answer.
156-215.80 Exam Question 102
The following graphic shows:
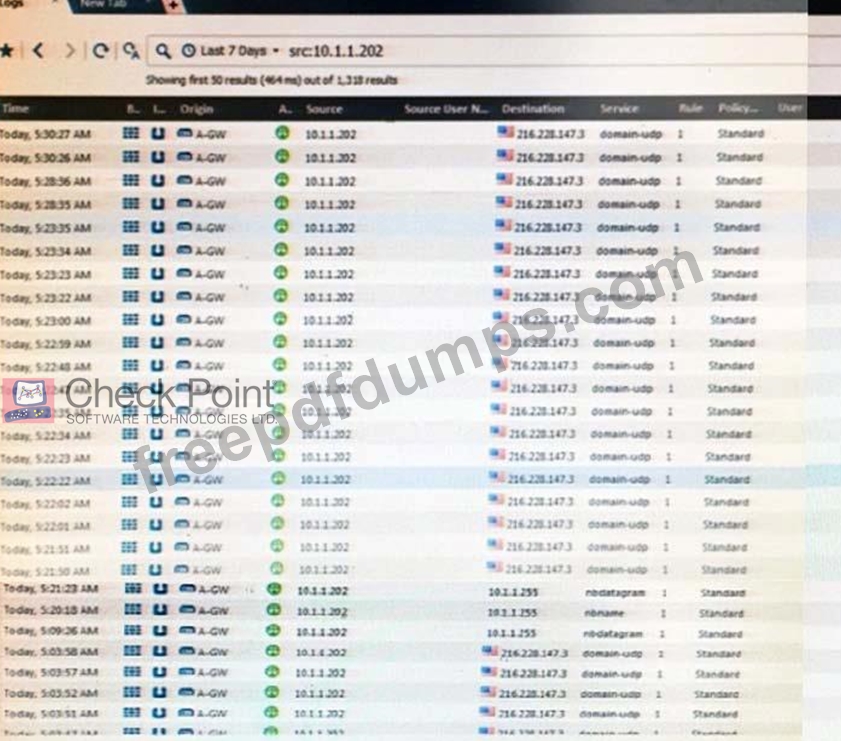

156-215.80 Exam Question 103
Which authentication scheme requires a user to possess a token?
156-215.80 Exam Question 104
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both
offices are protected by Check Point Security Gateway managed by the same Security Management Server.
While configuring the VPN community to specify the pre-shared secret the administrator found that the check
box to enable pre-shared secret is shared and cannot be enabled. Why does it not allow him to specify the
pre-shared secret?
offices are protected by Check Point Security Gateway managed by the same Security Management Server.
While configuring the VPN community to specify the pre-shared secret the administrator found that the check
box to enable pre-shared secret is shared and cannot be enabled. Why does it not allow him to specify the
pre-shared secret?
156-215.80 Exam Question 105
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
Premium Bundle
Newest 156-215.80 Exam PDF Dumps shared by Actual4test.com for Helping Passing 156-215.80 Exam! Actual4test.com now offer the updated 156-215.80 exam dumps, the Actual4test.com 156-215.80 exam questions have been updated and answers have been corrected get the latest Actual4test.com 156-215.80 pdf dumps with Exam Engine here:
(527 Q&As Dumps, 30%OFF Special Discount: Freepdfdumps)

