156-215.80 Exam Question 166
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
156-215.80 Exam Question 167
What is a role of Publishing?
156-215.80 Exam Question 168
Study the Rule base and Client Authentication Action properties screen.
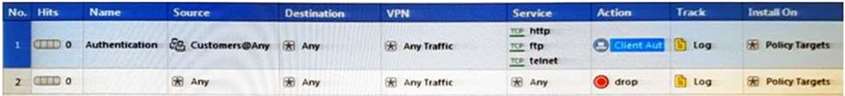
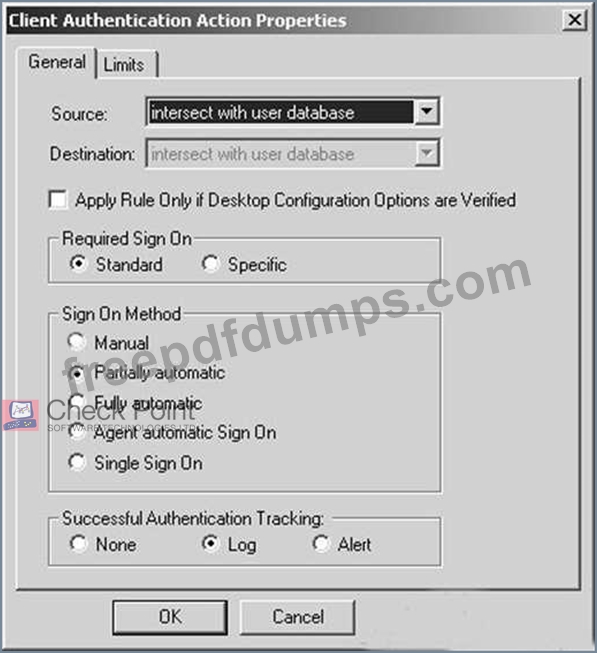
After being authenticated by the Security Gateways, a user starts a HTTP connection to a Web site. What happens when the user tries to FTP to another site using the command line? The:


After being authenticated by the Security Gateways, a user starts a HTTP connection to a Web site. What happens when the user tries to FTP to another site using the command line? The:
156-215.80 Exam Question 169
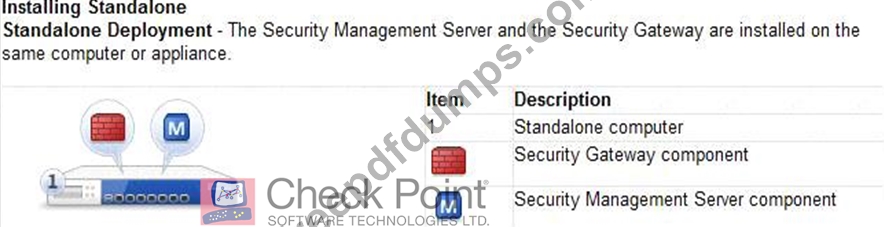
In which deployment is the security management server and Security Gateway installed on the same appliance?
156-215.80 Exam Question 170
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?