156-215.80 Exam Question 201
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to
HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, gateway policy permits access only from Join's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but the limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity
Sources.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, gateway policy permits access only from Join's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but the limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity
Sources.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
156-215.80 Exam Question 202
What will be the effect of running the following command on the Security Management
Server?
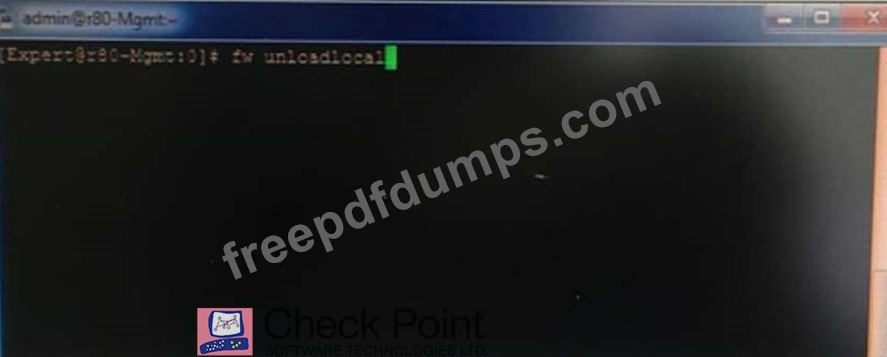
Server?

156-215.80 Exam Question 203
What are the two high availability modes?
156-215.80 Exam Question 204
Fill in the blank: The R80 feature ________ permits blocking specific IP addresses for a specified time period.
156-215.80 Exam Question 205
The system administrator of a company is trying to find out why acceleration is not working for the traffic.
The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated. What is the
most likely reason that the traffic is not accelerated?
The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated. What is the
most likely reason that the traffic is not accelerated?


