156-215.80 Exam Question 76
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
156-215.80 Exam Question 77
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
156-215.80 Exam Question 78
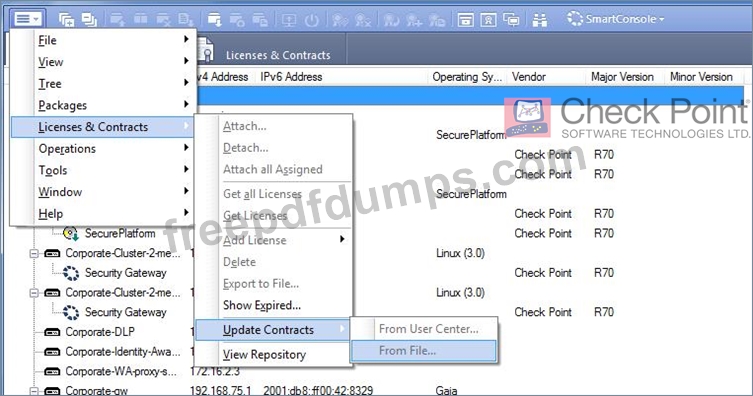
Which application should you use to install a contract file?
156-215.80 Exam Question 79
What is the default time length that Hit Count Data is kept?
156-215.80 Exam Question 80
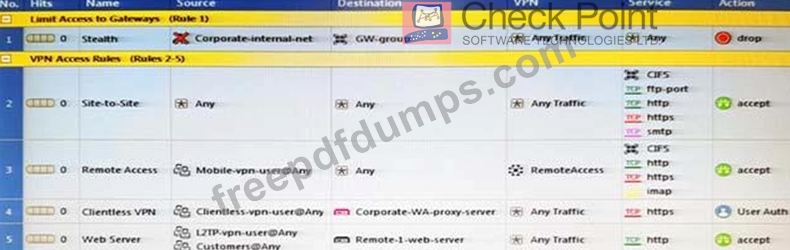
As you review this Security Policy, what changes could you make to accommodate Rule 4?