156-215.80 Exam Question 171
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
156-215.80 Exam Question 172
When using Monitored circuit VRRP, what is a priority delta?
156-215.80 Exam Question 173
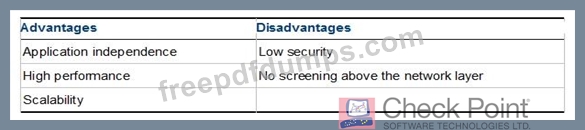
What is NOT an advantage of Packet Filtering?
156-215.80 Exam Question 174
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices
that there is a padlock sign next to the DNS rule in the Rule Base.
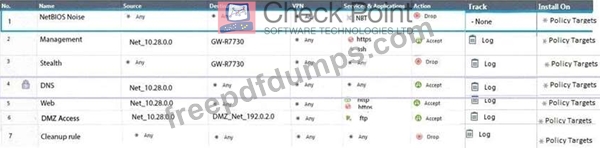
What is the possible explanation for this?
that there is a padlock sign next to the DNS rule in the Rule Base.

What is the possible explanation for this?
156-215.80 Exam Question 175
Check Point APIs allow system engineers and developers to make changes to their organization's security
policy with CLI tools and Web Services for all of the following except:
policy with CLI tools and Web Services for all of the following except: