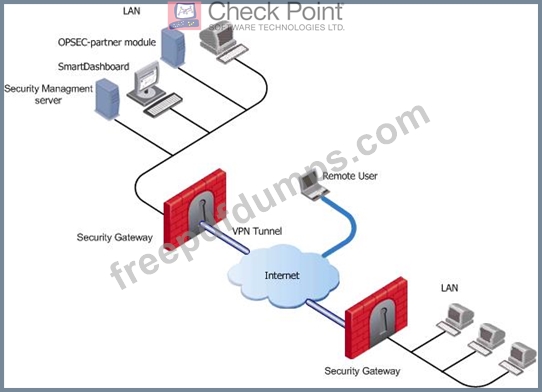
156-215.80 Exam Question 336
What are the three essential components of the Check Point Security Management Architecture?
156-215.80 Exam Question 337
Which Threat Prevention Profile is not included by default in R80 Management?
156-215.80 Exam Question 338
When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
156-215.80 Exam Question 339
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
156-215.80 Exam Question 340
Which of the following ClusterXL modes uses a non-unicast MAC address for the cluster IP address.