156-215.80 Exam Question 396
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
156-215.80 Exam Question 397
What are the two types of NAT supported by the Security Gateway?
156-215.80 Exam Question 398
Joey is using the computer with IP address 192.168.20.13. He wants to access web page
"www.CheckPoint.com", which is hosted on Web server with IP address 203.0.113.111. How many rules on
Check Point Firewall are required for this connection?
"www.CheckPoint.com", which is hosted on Web server with IP address 203.0.113.111. How many rules on
Check Point Firewall are required for this connection?
156-215.80 Exam Question 399
You are working with multiple Security Gateways enforcing an extensive number of rules. To simplify security administration, which action would you choose?
156-215.80 Exam Question 400
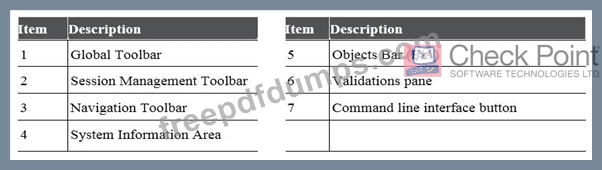
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?