156-215.80 Exam Question 251
Which Check Point software blade provides visibility of users, groups and machines while also providing access control through identity-based policies?
156-215.80 Exam Question 252
At what point is the Internal Certificate Authority (ICA) created?
156-215.80 Exam Question 253
On the following picture an administrator configures Identity Awareness:
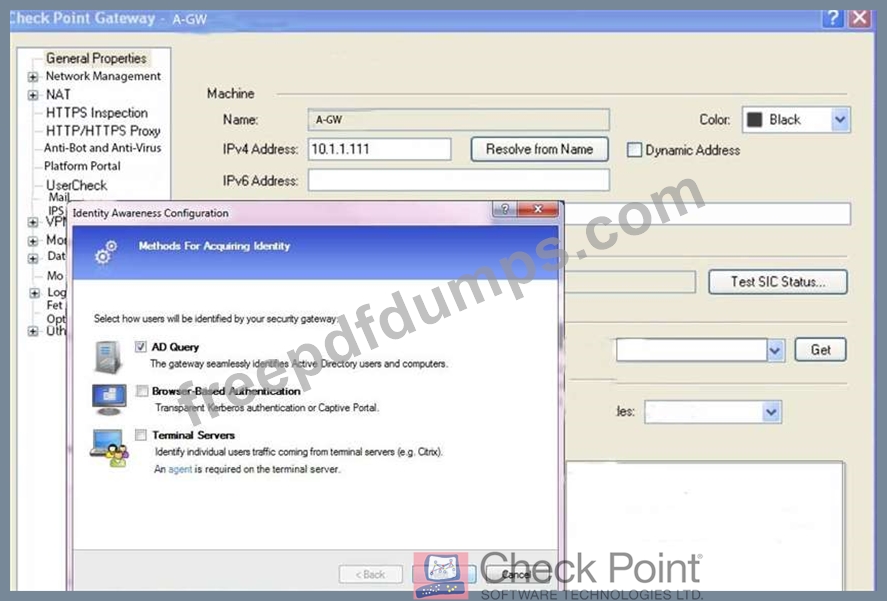
After clicking "Next" the above configuration is supported by:

After clicking "Next" the above configuration is supported by:
156-215.80 Exam Question 254
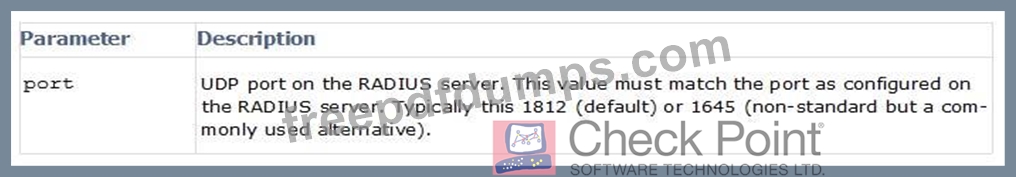
Fill in the blank: RADIUS protocol uses ______ to communicate with the gateway.
156-215.80 Exam Question 255
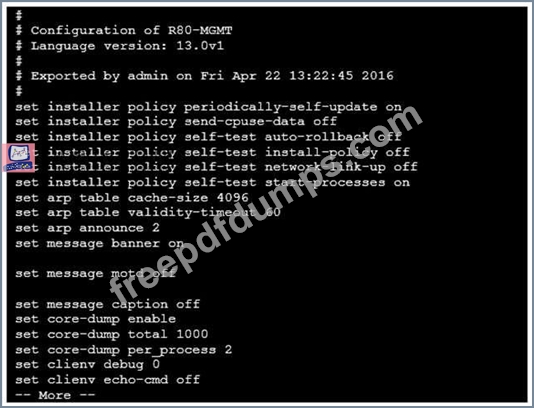
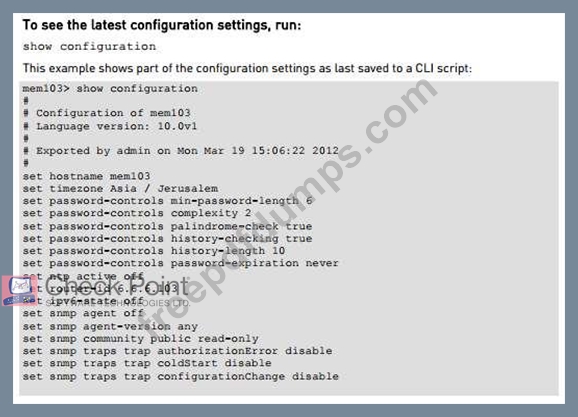
Look at the screenshot below. What CLISH command provides this output?