156-215.80 Exam Question 306
rd
According to Check Point Best Practice, when adding a 3 party gateway to a Check Point security solution what object SHOULD be added? A(n):
According to Check Point Best Practice, when adding a 3 party gateway to a Check Point security solution what object SHOULD be added? A(n):
156-215.80 Exam Question 307
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?
156-215.80 Exam Question 308
To create policy for traffic to or from a particular location, use the _____________.
156-215.80 Exam Question 309
Review the rules. Assume domain UDP is enabled in the implied rules.
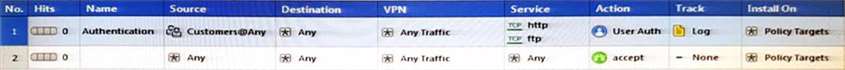
What happens when a user from the internal network tries to browse to the internet using HTTP? The user:

What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
156-215.80 Exam Question 310
To enforce the Security Policy correctly, a Security Gateway requires:

