200-201 Exam Question 41
Refer to the exhibit.

What is the potential threat identified in this Stealthwatch dashboard?

What is the potential threat identified in this Stealthwatch dashboard?
200-201 Exam Question 42
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
200-201 Exam Question 43
What does cyber attribution identity in an investigation?
200-201 Exam Question 44
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.
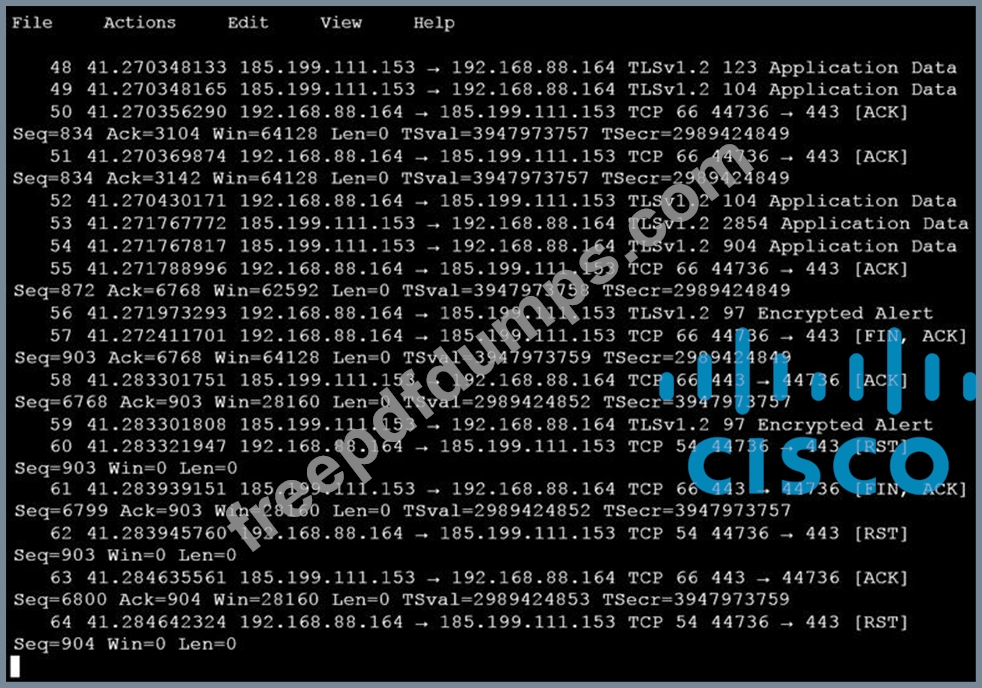
Which obfuscation technique is the attacker using?

Which obfuscation technique is the attacker using?
200-201 Exam Question 45
Which security technology allows only a set of pre-approved applications to run on a system?

