200-201 Exam Question 1
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
Which technology makes this behavior possible?
200-201 Exam Question 2
W[^t is vulnerability management?
200-201 Exam Question 3
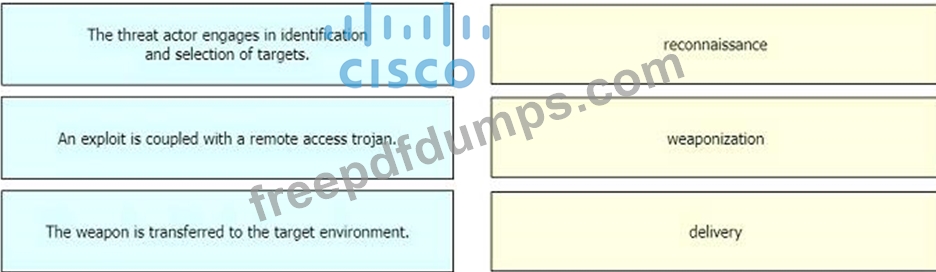
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.

200-201 Exam Question 4
Refer to the exhibit.

Which type of attack is being executed?

Which type of attack is being executed?
200-201 Exam Question 5
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
Which information is available on the server certificate?


