200-201 Exam Question 1
Refer to the exhibit.
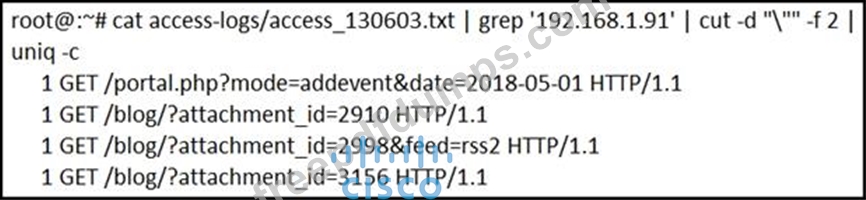
What is depicted in the exhibit?

What is depicted in the exhibit?
200-201 Exam Question 2
Refer to the exhibit.
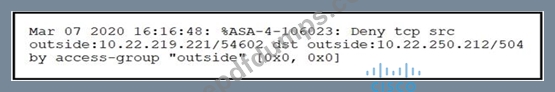
Which technology generates this log?

Which technology generates this log?
200-201 Exam Question 3
Which vulnerability type is used to read, write, or erase information from a database?
200-201 Exam Question 4
What does an attacker use to determine which network ports are listening on a potential target device?
200-201 Exam Question 5
Which information must an organization use to understand the threats currently targeting the organization?

