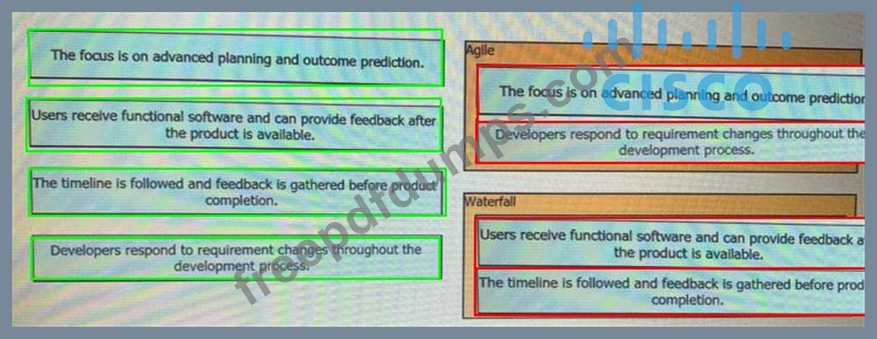
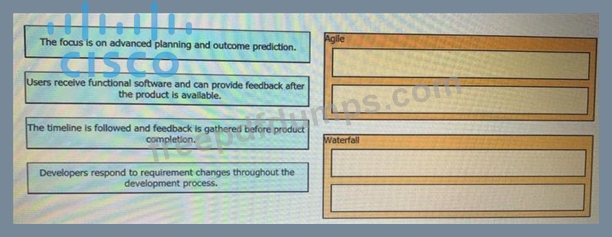
200-901 Exam Question 1
Drag and drop the characteristics from the left onto the corresponding software development methodologies on the right?

200-901 Exam Question 2
Which task is performed because the test-driven development approach is being used?
200-901 Exam Question 3
Refer to the exhibit.
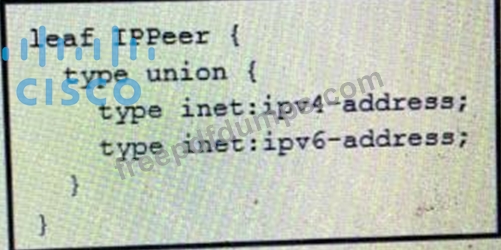
What is the value of the node defined by this YANG structure?
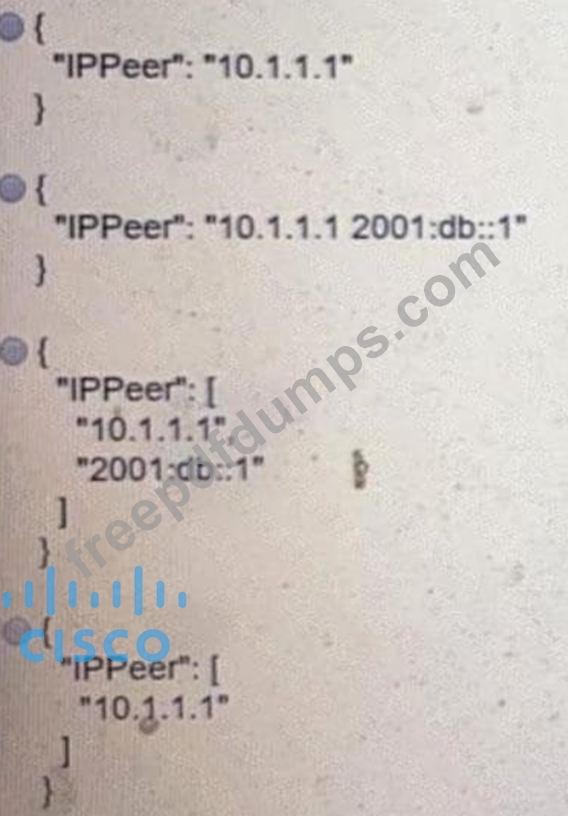

What is the value of the node defined by this YANG structure?

200-901 Exam Question 4
Which type of threat occur when an attacker can send hostile data to an interpreter within an application?
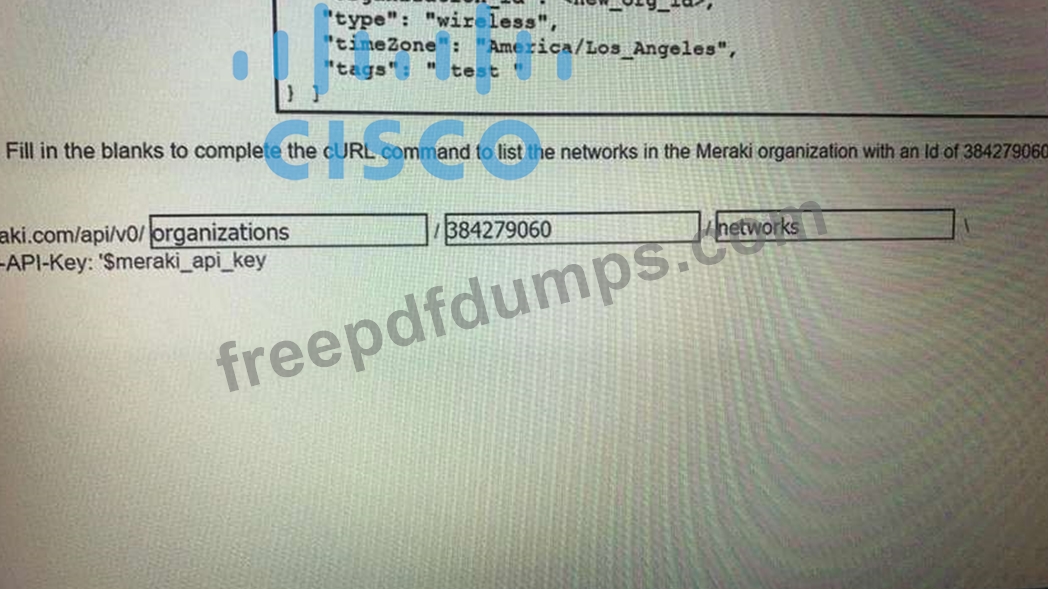
200-901 Exam Question 5
Refer to the exhibit.
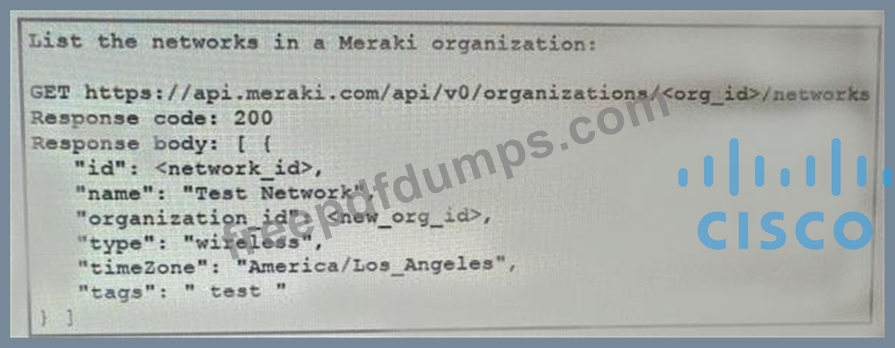
Fill in the blanks to complete the cURL command to the list of networks in the Meraki organization with an id of 384279060


Fill in the blanks to complete the cURL command to the list of networks in the Meraki organization with an id of 384279060