300-715 Exam Question 86
A network engineer needs to ensure that the access credentials are not exposed during the 802.1x authentication among components. Which two protocols should complete this task?
300-715 Exam Question 87
A network administrator changed a Cisco ISE deployment from pilot to production and noticed that the JVM memory utilization increased significantly. The administrator suspects this is due to replication between the nodes What must be configured to minimize performance degradation?
300-715 Exam Question 88
Which two values are compared by the binary comparison (unction in authentication that is based on Active Directory?
300-715 Exam Question 89
Refer to the exhibit.
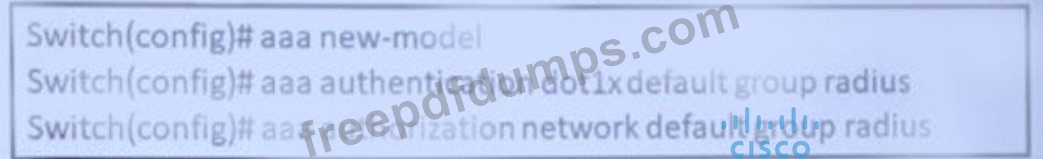
A network engineers configuring the switch to accept downloadable ACLs from a Cisco ISC server Which two commands should be run to complete the configuration? (Choose two)

A network engineers configuring the switch to accept downloadable ACLs from a Cisco ISC server Which two commands should be run to complete the configuration? (Choose two)
300-715 Exam Question 90
Which two ports do network devices typically use for CoA? (Choose two.)

