300-715 Exam Question 31
Which use case validates a change of authorization?
300-715 Exam Question 32
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
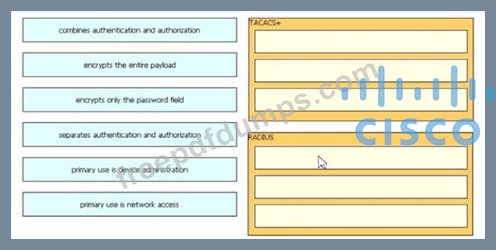

300-715 Exam Question 33
A laptop was stolen and a network engineer added it to the block list endpoint identity group.
What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
300-715 Exam Question 34
What is a difference between TACACS+ and RADIUS in regards to encryption?
300-715 Exam Question 35
Which two actions occur when a Cisco ISE server device administrator logs in to a device?
(Choose two)
(Choose two)


