350-201 Exam Question 36
An engineer wants to review the packet overviews of SNORT alerts. When printing the SNORT alerts, all the packet headers are included, and the file is too large to utilize. Which action is needed to correct this problem?
350-201 Exam Question 37
A customer is using a central device to manage network devices over SNMPv2. A remote attacker caused a denial of service condition and can trigger this vulnerability by issuing a GET request for the ciscoFlashMIB OID on an affected device. Which should be disabled to resolve the issue?
350-201 Exam Question 38
Refer to the exhibit.
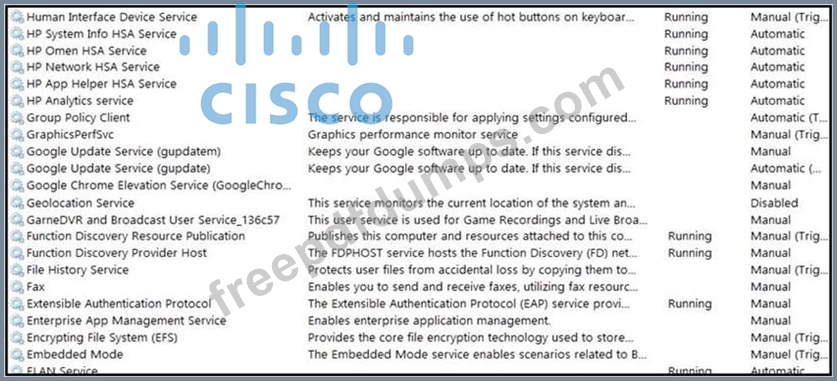
An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon - Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?

An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon - Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?
350-201 Exam Question 39
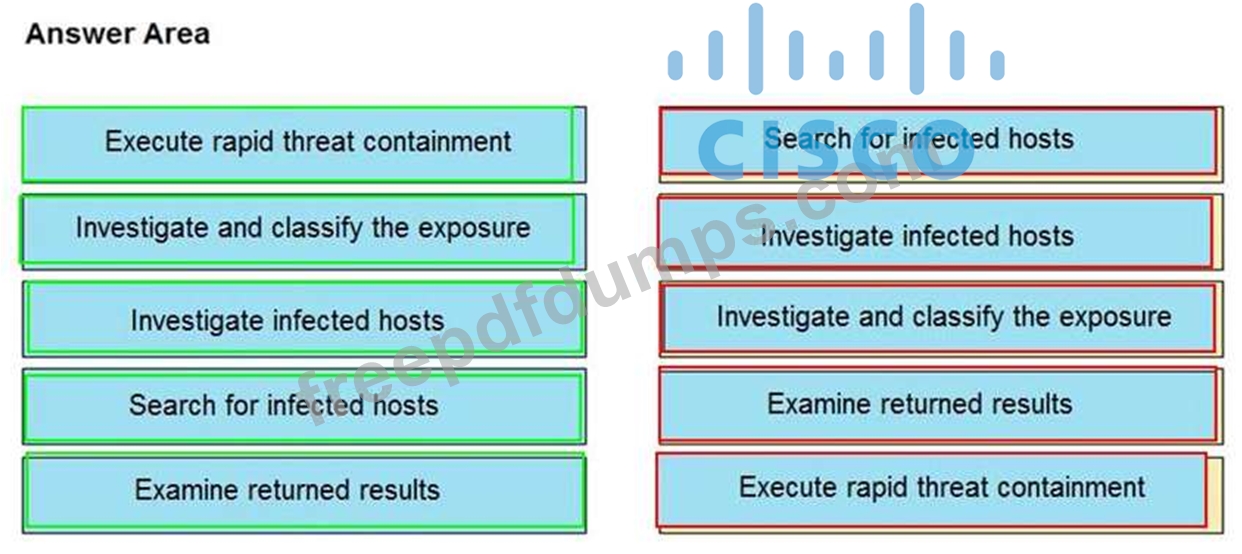
Refer to the exhibit.
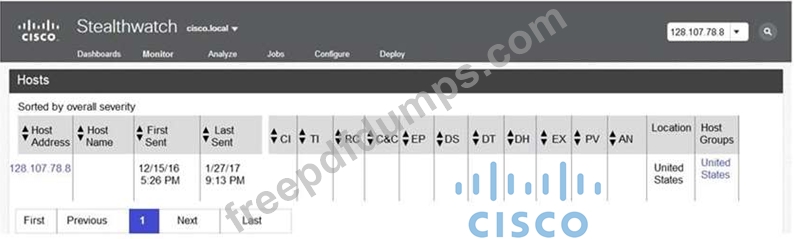
The Cisco Secure Network Analytics (Stealthwatch) console alerted with "New Malware Server Discovered" and the IOC indicates communication from an end-user desktop to a Zeus C&C Server. Drag and drop the actions that the analyst should take from the left into the order on the right to investigate and remediate this IOC.
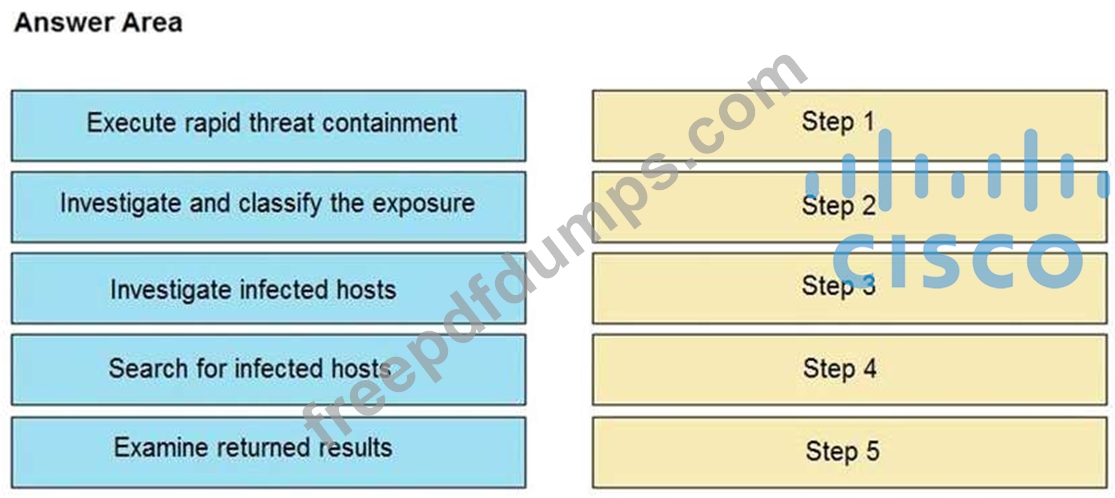

The Cisco Secure Network Analytics (Stealthwatch) console alerted with "New Malware Server Discovered" and the IOC indicates communication from an end-user desktop to a Zeus C&C Server. Drag and drop the actions that the analyst should take from the left into the order on the right to investigate and remediate this IOC.

350-201 Exam Question 40
A SIEM tool fires an alert about a VPN connection attempt from an unusual location. The incident response team validates that an attacker has installed a remote access tool on a user's laptop while traveling. The attacker has the user's credentials and is attempting to connect to the network.
What is the next step in handling the incident?
What is the next step in handling the incident?
Premium Bundle
Newest 350-201 Exam PDF Dumps shared by Actual4test.com for Helping Passing 350-201 Exam! Actual4test.com now offer the updated 350-201 exam dumps, the Actual4test.com 350-201 exam questions have been updated and answers have been corrected get the latest Actual4test.com 350-201 pdf dumps with Exam Engine here:
(141 Q&As Dumps, 30%OFF Special Discount: Freepdfdumps)