350-901 Exam Question 106
Which two strategies are used to protect personally identifiable information? (Choose two.)
350-901 Exam Question 107
Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX Device, Not all options are used


350-901 Exam Question 108
Which statement about microservices architecture is true?
350-901 Exam Question 109
Refer to the exhibit.
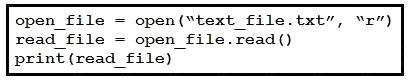
A developer created the code, but it fails toexecute. Which code snippet helps to identify the issue?
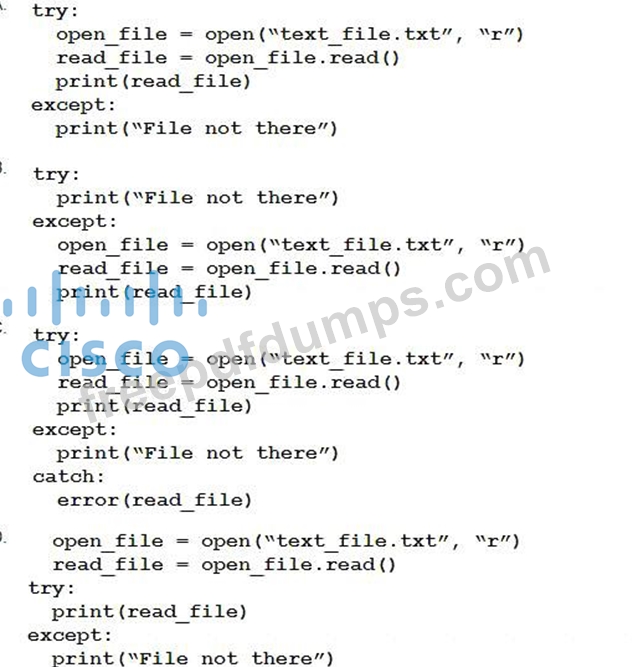

A developer created the code, but it fails toexecute. Which code snippet helps to identify the issue?

350-901 Exam Question 110
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow?
(Choose two.)
(Choose two.)


