350-901 Exam Question 121
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
350-901 Exam Question 122
Drag and Drop Question
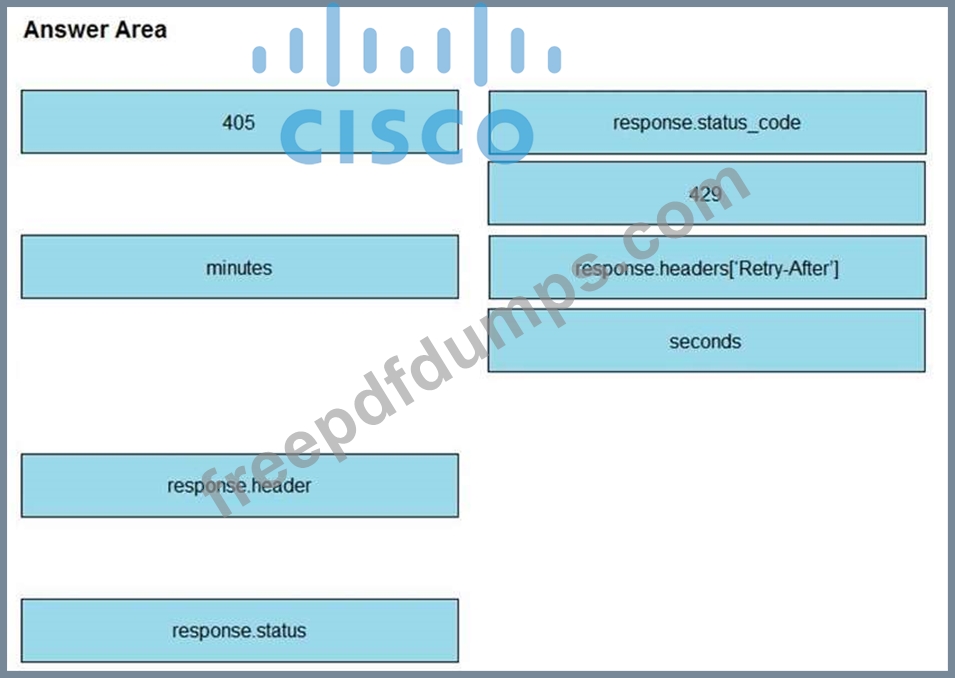
Refer to the exhibit. A developer is creating a Python script to use the Webex Teams REST API to list joined spaces, retry after the server-specified amount of time if a "Too many requests" response is received, and print any other error that is received. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script. Not all code snippets are used.
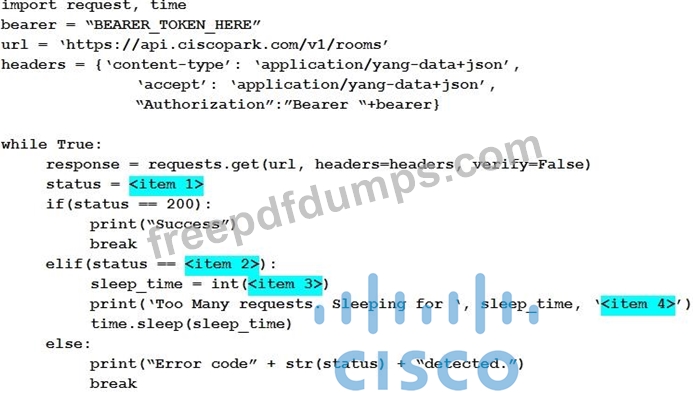
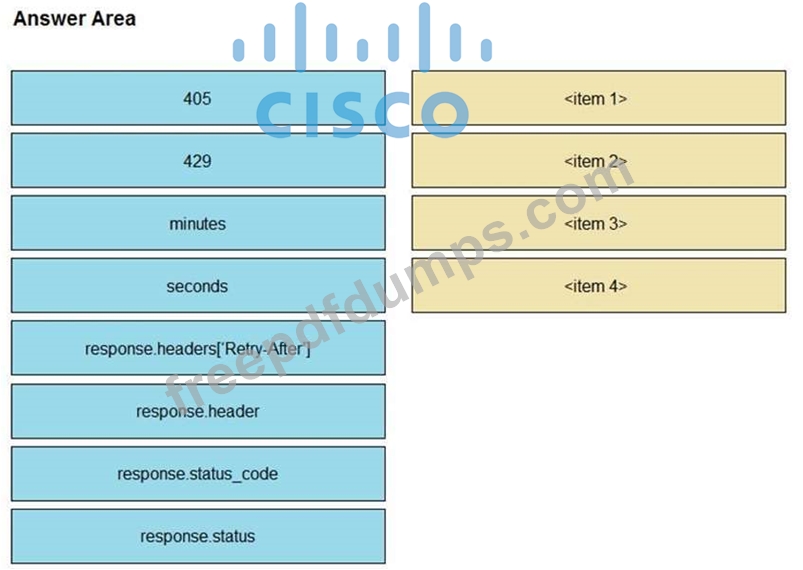
Refer to the exhibit. A developer is creating a Python script to use the Webex Teams REST API to list joined spaces, retry after the server-specified amount of time if a "Too many requests" response is received, and print any other error that is received. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script. Not all code snippets are used.


350-901 Exam Question 123
Refer to the exhibit.
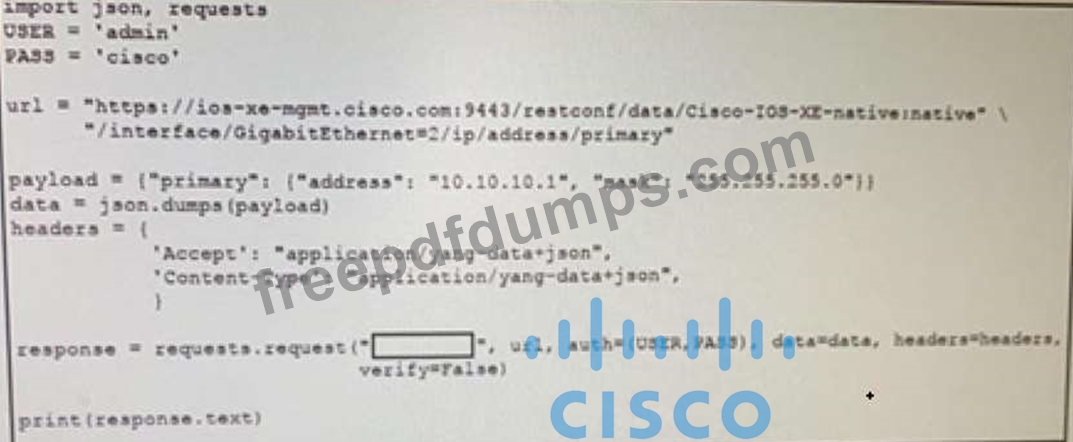
Which RESTCONF verb changes the GigabitEthernet2 interface from 192.168.100.1/24 to 10.10.10.1/24

Which RESTCONF verb changes the GigabitEthernet2 interface from 192.168.100.1/24 to 10.10.10.1/24
350-901 Exam Question 124
Refer to the exhibits which show the documentation associated with the create port object API call in Cisco Firepower Threat Defense, and a cURL command.
Which data payload completes the cURL command to run the API call?
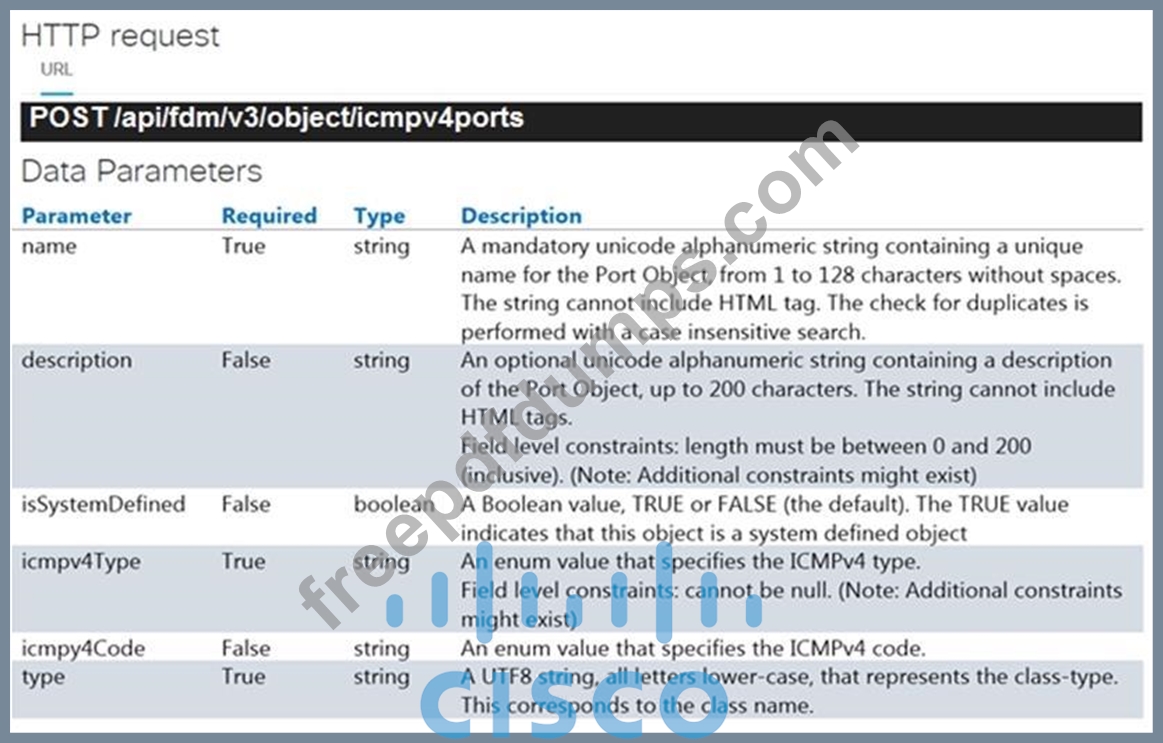
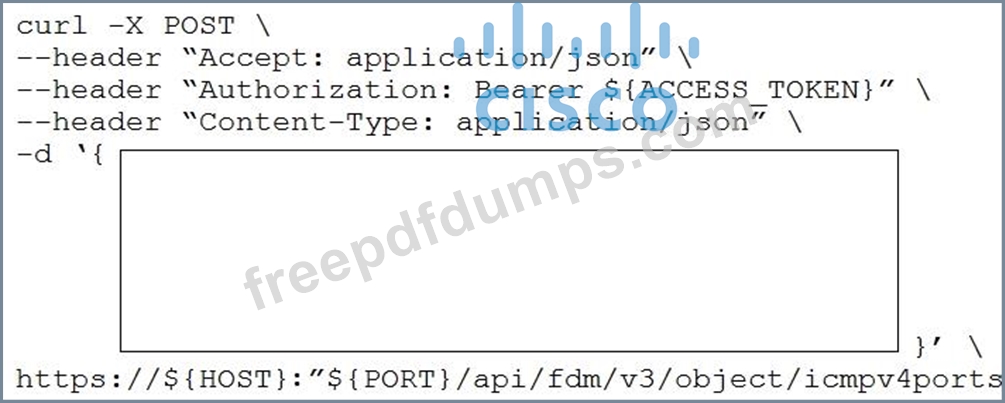
Which data payload completes the cURL command to run the API call?


350-901 Exam Question 125
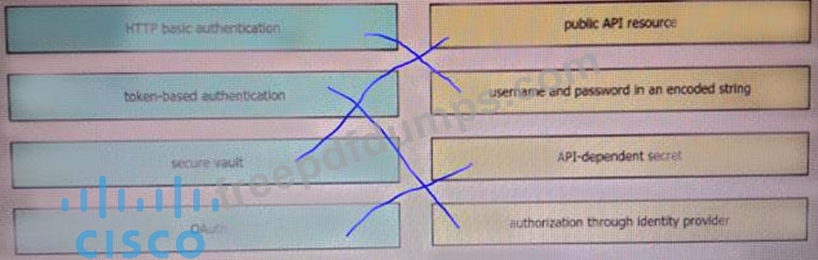
Drag and drop the REST API authentication method from the left to the description on the right