350-901 Exam Question 36
Refer to the exhibit.
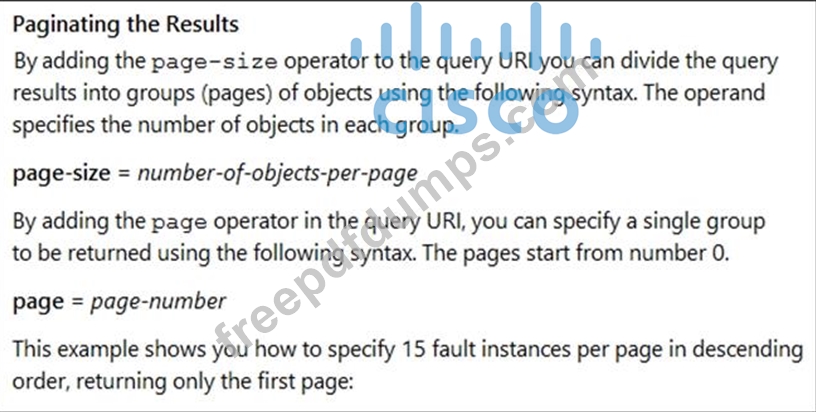
Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?

Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
350-901 Exam Question 37
Which two techniques protect against injection attacks? (Choose two.)
350-901 Exam Question 38
What are two steps in the OAuth2 protocol flow? (Choose two.)
350-901 Exam Question 39
Refer to the exhibit.

A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2 The number of client entries per returned page is restricted to 1.000 according to the API specification Network 2 has 2.500 clients What must be added where the code is missing to print the content of each response?
A)

B)

C)
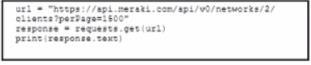
D)
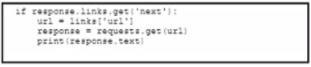

A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2 The number of client entries per returned page is restricted to 1.000 according to the API specification Network 2 has 2.500 clients What must be added where the code is missing to print the content of each response?
A)

B)

C)

D)

350-901 Exam Question 40
Which two design considerations should be considered when building a Cisco Meraki dashboard out of available APIs? (Choose two,)

