350-901 Exam Question 1
Application sometimes store configuration as constants in the code, which is a violation of strict separation of configuration from code. Where should application configuration be stored?
350-901 Exam Question 2
Refer of the exhibit.
Click on the resource labs in the top left corner to view resources to help with this question The script uses the Cisco Intersight REST API Drag and drop the code from the bottom of the code snippet to the blanks in the code to construct a Python script to update the firmware on a specific Cisco interaght managed UCS rack server, DMZ-RL3ADJM.
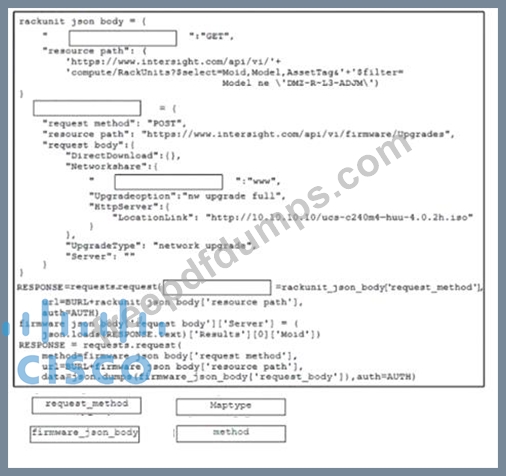
Click on the resource labs in the top left corner to view resources to help with this question The script uses the Cisco Intersight REST API Drag and drop the code from the bottom of the code snippet to the blanks in the code to construct a Python script to update the firmware on a specific Cisco interaght managed UCS rack server, DMZ-RL3ADJM.

350-901 Exam Question 3
Refer to the exhibit.
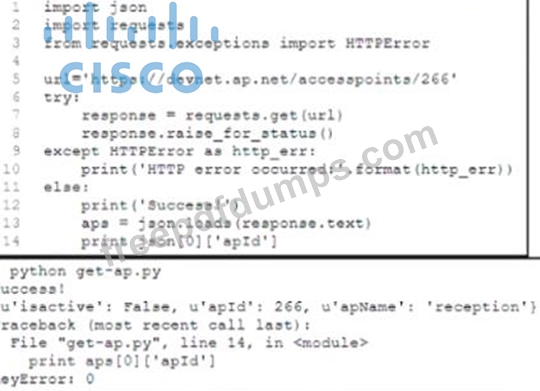
A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points The developer is retrieving an access point ID by using a REST API The output indicates that there was a KeyError when parsing the JSON response. What returns the expected output of 266 at line 14?
A)

B)

C)

D)


A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points The developer is retrieving an access point ID by using a REST API The output indicates that there was a KeyError when parsing the JSON response. What returns the expected output of 266 at line 14?
A)

B)

C)

D)

350-901 Exam Question 4
Which two encryption principles should be applied to secure APIs? (Choose two.)
350-901 Exam Question 5
Refer to the exhibit A script returns the location of a specific access point when given the access point name If a user enters a search value such as DROP TABLE access points then the entire table is removed. What must be added to the box where the code is missing to prevent a SQL injection attack?
A)

B)

C)

D)

A)

B)

C)

D)



