350-901 Exam Question 131
Refer to the exhibit.
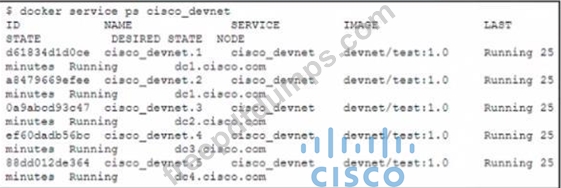
The cisco_devnet Docker swarm service runs across five replicas The development team tags and imports a new image named devnet'test 1 1 and requests that the image be upgraded on each container There must be no service outages during the upgrade process Which two design approaches must be used? (Choose two.)

The cisco_devnet Docker swarm service runs across five replicas The development team tags and imports a new image named devnet'test 1 1 and requests that the image be upgraded on each container There must be no service outages during the upgrade process Which two design approaches must be used? (Choose two.)
350-901 Exam Question 132
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
350-901 Exam Question 133
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
Which two actions can improve the design of the application to identify the faults? (Choose two.)
350-901 Exam Question 134
When an application is designed that requires high availability, what is a reason to use a cross-region cloud?
350-901 Exam Question 135
Refer to the exhibit.

An application's REST API GET call is tested to the inventory database. Which missing code must be included to limit the number of values that are returned from the query to 20?

An application's REST API GET call is tested to the inventory database. Which missing code must be included to limit the number of values that are returned from the query to 20?

