350-901 Exam Question 36
Which two encryption principles should be applied to secure APIs? (Choose two.)
350-901 Exam Question 37
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow?
(Choose two.)
(Choose two.)
350-901 Exam Question 38
Refer to the exhibit.
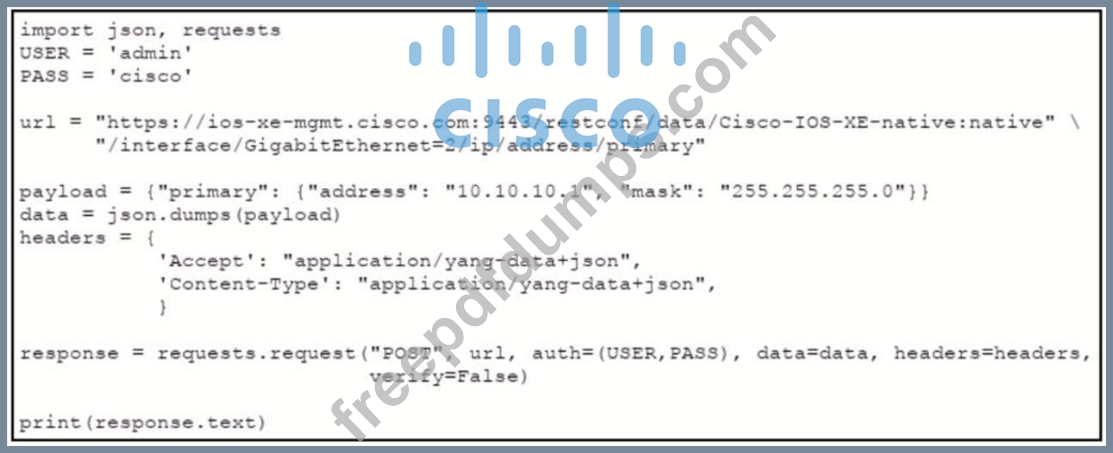
An engineer needs to change the IP address via RESTCOMF on interface GigabitEthernet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?

An engineer needs to change the IP address via RESTCOMF on interface GigabitEthernet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?
350-901 Exam Question 39
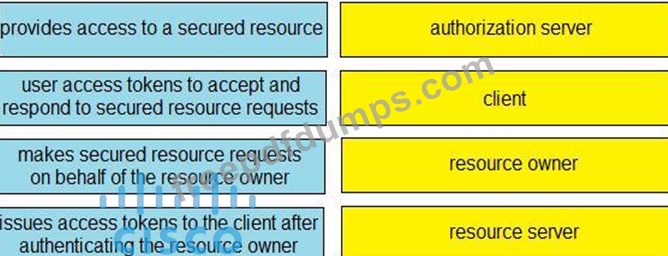
Drag and drop the descriptions from the left onto the related OAuth-defined roles on the right.

350-901 Exam Question 40
A developer is deploying an application to automate the configuration and management of Osco network files and routers The application must use REST API interface lo achieve programmability. The security team mandates that the network must be protected against DDoS attacks What mitigates the attacks without impacting genuine requests?