352-001 Exam Question 106
A company wants to use SSM as the multicast routing protocol inside its network. Some of its multicast applications do not support IGMPv3. In which two ways can the mapping be done when these applications send IGMPv2 join messages? (Choose two.)
352-001 Exam Question 107
Refer to the exhibit.
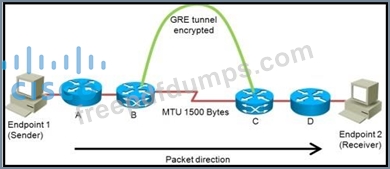
You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C.
The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C.
If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations?
(Choose three.)

You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C.
The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C.
If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations?
(Choose three.)
352-001 Exam Question 108
You are a network designer and have been asked to consult with your server operations team to further enhance the security of the network. The operations team provides you with these details about the network:
A pool of servers is accessed by numerous data centers and remote sites. The servers are accessed via a cluster of firewalls. The firewalls are configured properly and are not dropping traffic. The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology would you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
A pool of servers is accessed by numerous data centers and remote sites. The servers are accessed via a cluster of firewalls. The firewalls are configured properly and are not dropping traffic. The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology would you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
352-001 Exam Question 109
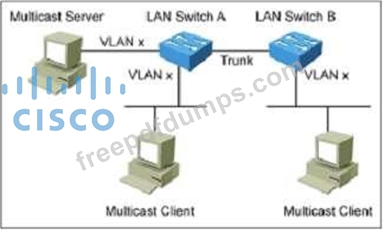
Refer to the exhibit. Which two features can be used to make multicast work in this situation? (Choose two.)

352-001 Exam Question 110
Which three network management requirements are common practices in network design? (Choose Two)

