400-007 Exam Question 71
The major business applications of an enterprise are largely monolithic and hard-coded As part of a major modernization and overhaul of the applications the goal is to move to a modular and containerized application architecture mode At the same time decoupling from the hardware is desired to move to an on-demand provisioning However the CyberOps team mandated that the final architecture must provide the same security levels as an air-gapped data center. Which cloud architecture meets these requirements?
400-007 Exam Question 72
Company XYZ has 30 sites using MPLS L3 VPN and the company is now concerned about data integrity. The company wants to redesign the security aspect of their network based on these requirements:
* Securely transfer the corporate data over the private WAN
* Use a centralized configuration model.
* Minimize overhead on the tunneled traffic.
Which technology can be used in the new design to meet the company's requirements?
* Securely transfer the corporate data over the private WAN
* Use a centralized configuration model.
* Minimize overhead on the tunneled traffic.
Which technology can be used in the new design to meet the company's requirements?
400-007 Exam Question 73
A company requires an RPO of less than 10 seconds to ensure business continuity. Which technology should be deployed?
400-007 Exam Question 74
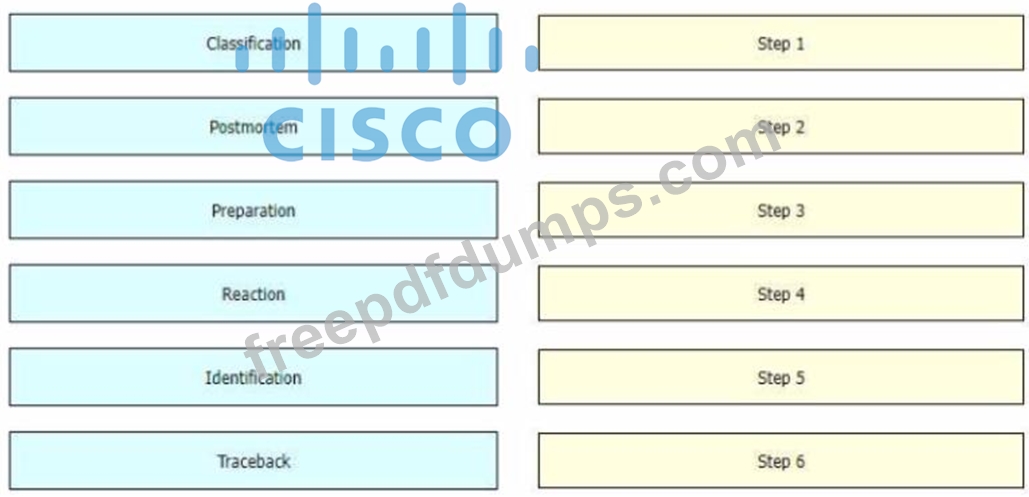
While computer networks and sophisticated applications have allowed individuals to be more productive the need to prepare for security threats has increased dramatically A six-step methodology on security incident handling has been adopted by many organizations including service providers enterprises, and government organizations to ensure that organizations are aware of significant security incidents and act quickly to stop the attacker, minimize damage caused, and prevent follow on attacks or similar incidents in the future Drag and drop the actions on the left to the targets on the right in the correct order.

400-007 Exam Question 75
Which statement about OSPF hub-and-spoke topology is true?


