400-007 Exam Question 111
Company XYZ wants to improve the security design of their network to include protection from reconnaissance and DoS attacks on their sub interfaces destined toward next hop routers. Which technology can be used to prevent these types of attacks?
400-007 Exam Question 112
What is a disadvantage of the traditional three-tier architecture model when east west traffic between different pods must go through the distribution and core layers?
400-007 Exam Question 113
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. Recently, they added a new branch to their network. Due to physical security concerns, they want to extend their existing IP CCTV network of the head office to the new branch, without any routing changes in the network. They are also under some time constraints. What is the best approach to extend the existing IP CCTV network to the new branch, without incurring any IP address changes?
400-007 Exam Question 114
You want to mitigate failures that are caused by STP loops that occur before UDLD detects the failure or that are caused by a device that is no longer sending BPDUs. Which mechanism do you use along with UDLD?
400-007 Exam Question 115
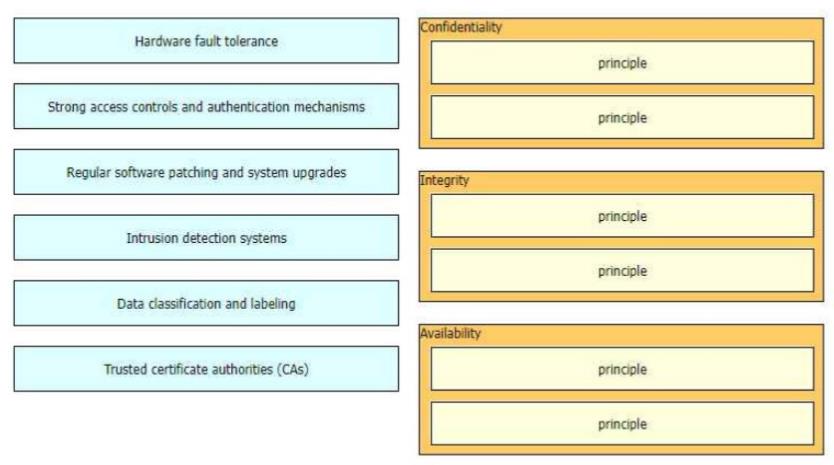
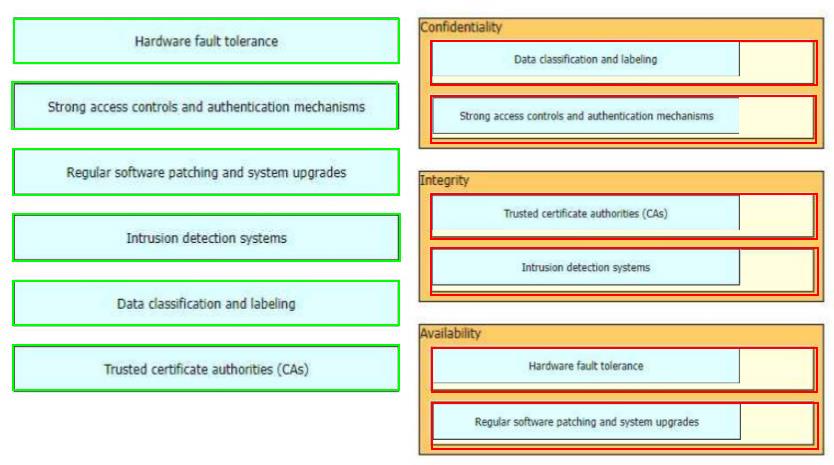
The CIA triad is foundational to information security, and one can be certain that one or more of the principles within the CIA triad has been violated when data is leaked or a system is attacked Drag and drop the countermeasures on the left to the appropriate principle section on the right in any order