400-007 Exam Question 31
Company XYZ has a new network based on IPv6. Some of the subnets that they are planning to use will be confidential and need an addressing scheme that confines them to the local campus network. Which type of IPv6 addresses can be used for these networks in the IPv6 addressing design?
400-007 Exam Question 32
An enterprise service provider is designing the network for a customer who runs a video application in both a centralized and distributed fashion The team has looked at the following parameters
*The available bandwidth for branches and the associated cost
*Video resource cost
*Usage patterns at hub-and-spoke sites.
*Call agent bridge selection algorithm
Which key piece of information is missing and needs to be taken into consideration in order to determine the correct resource allocation model?
*The available bandwidth for branches and the associated cost
*Video resource cost
*Usage patterns at hub-and-spoke sites.
*Call agent bridge selection algorithm
Which key piece of information is missing and needs to be taken into consideration in order to determine the correct resource allocation model?
400-007 Exam Question 33
Most security monitoring systems use a signature-based approach to detect threats In which two instances are systems based on Network Behavior Anomaly Detection better than signature-based systems when it comes to detecting security threat vectors'? (Choose two.)
400-007 Exam Question 34
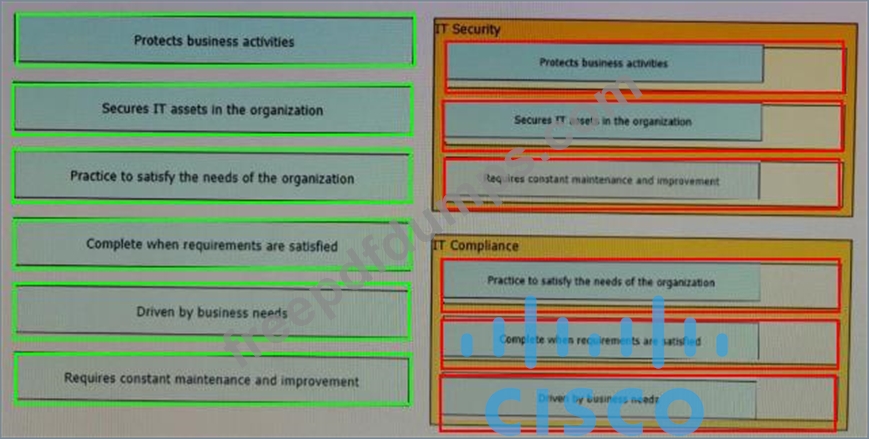
The line between security and compliance is easily blurred and is, to a large extent, a moving target Drag and drop each of the requirements on the left to the appropriate section on the right


400-007 Exam Question 35
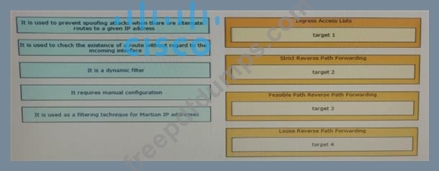
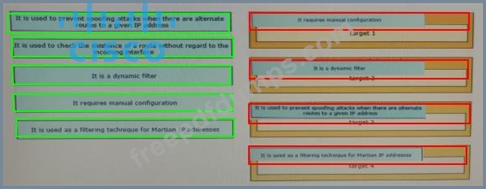
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.