CAS-004 Exam Question 26
A security analyst needs to recommend a remediation to the following threat:
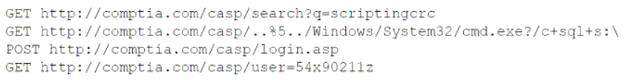
Which of the following actions should the security analyst propose to prevent this successful exploitation?

Which of the following actions should the security analyst propose to prevent this successful exploitation?
CAS-004 Exam Question 27
A company just released a new video card. Due to limited supply and high demand, attackers are employing automated systems to purchase the device through the company's web store so they can resell it on the secondary market. The company's intended customers are frustrated. A security engineer suggests implementing a CAPTCHA system on the web store to help reduce the number of video cards purchased through automated systems. Which of the following now describes the level of risk?
CAS-004 Exam Question 28
An IT administrator is reviewing all the servers in an organization and notices that a server is missing crucial practice against a recent exploit that could gain root access.
Which of the following describes the administrator's discovery?
Which of the following describes the administrator's discovery?
CAS-004 Exam Question 29
A company has moved its sensitive workloads lo the cloud and needs to ensure high availability and resiliency of its web-based application. The cloud architecture team was given the following requirements
* The application must run at 70% capacity at all times
* The application must sustain DoS and DDoS attacks.
* Services must recover automatically.
Which of the following should the cloud architecture team implement? (Select THREE).
* The application must run at 70% capacity at all times
* The application must sustain DoS and DDoS attacks.
* Services must recover automatically.
Which of the following should the cloud architecture team implement? (Select THREE).
CAS-004 Exam Question 30
A developer wants to develop a secure external-facing web application. The developer is looking for an online community that produces tools, methodologies, articles, and documentation in the field of web-application security Which of the following is the BEST option?

