CAS-005 Exam Question 31
A vulnerability can on a web server identified the following:
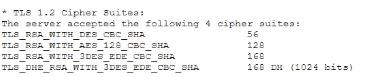
Which of the following actions would most likely eliminate on path decryption attacks? (Select two).

Which of the following actions would most likely eliminate on path decryption attacks? (Select two).
CAS-005 Exam Question 32
A security engineer is assisting a DevOps team that has the following requirements for container images:
Ensure container images are hashed and use version controls.
Ensure container images are up to date and scanned for vulnerabilities.
Which of the following should the security engineer do to meet these requirements?
Ensure container images are hashed and use version controls.
Ensure container images are up to date and scanned for vulnerabilities.
Which of the following should the security engineer do to meet these requirements?
CAS-005 Exam Question 33
While reviewing recent modem reports, a security officer discovers that several employees were contacted by the same individual who impersonated a recruiter. Which of the following best describes this type of correlation?
CAS-005 Exam Question 34
A systems engineer is configuring a system baseline for servers that will provide email services. As part of the architecture design, the engineer needs to improve performance of the systems by using an access vector cache, facilitating mandatory access control and protecting against:
* Unauthorized reading and modification of data and programs
* Bypassing application security mechanisms
* Privilege escalation
* interference with other processes
Which of the following is the most appropriate for the engineer to deploy?
* Unauthorized reading and modification of data and programs
* Bypassing application security mechanisms
* Privilege escalation
* interference with other processes
Which of the following is the most appropriate for the engineer to deploy?
CAS-005 Exam Question 35
A company hosts a platform-as-a-service solution with a web-based front end, through which customer interact with data sets. A security administrator needs to deploy controls to prevent application-focused attacks. Which of the following most directly supports the administrator's objective'

