PT0-002 Exam Question 1
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
PT0-002 Exam Question 2
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company's servers. Which of the following actions would BEST enable the tester to perform phishing in a later stage of the assessment?
PT0-002 Exam Question 3
The following PowerShell snippet was extracted from a log of an attacker machine:
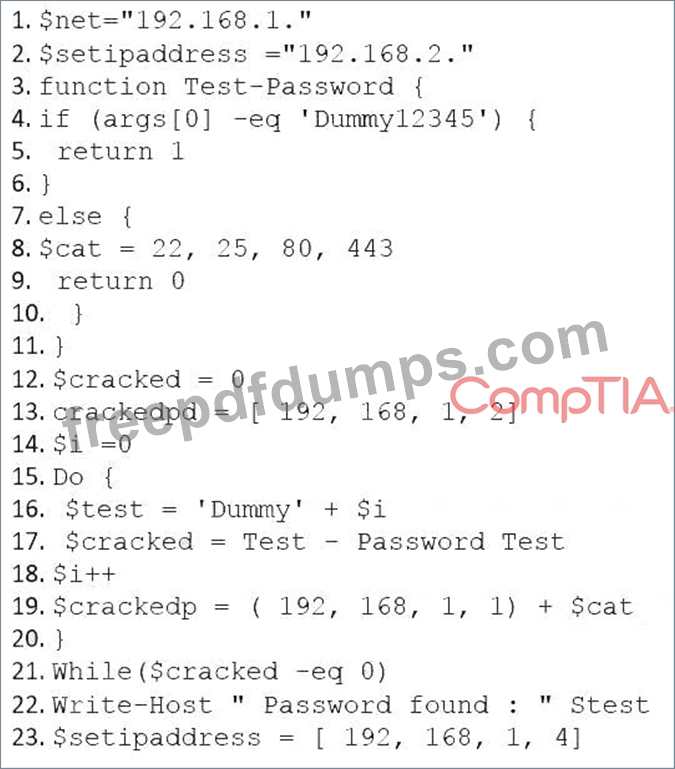
A penetration tester would like to identify the presence of an array. Which of the following line numbers would define the array?

A penetration tester would like to identify the presence of an array. Which of the following line numbers would define the array?
PT0-002 Exam Question 4
During an assessment, a penetration tester found a suspicious script that could indicate a prior compromise.
While reading the script, the penetration tester noticed the following lines of code:
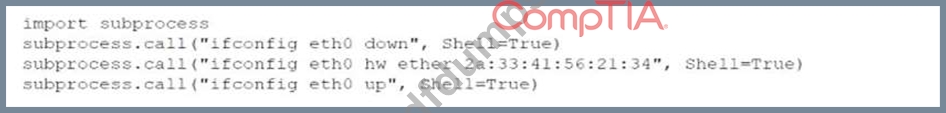
Which of the following was the script author trying to do?
While reading the script, the penetration tester noticed the following lines of code:

Which of the following was the script author trying to do?
PT0-002 Exam Question 5
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
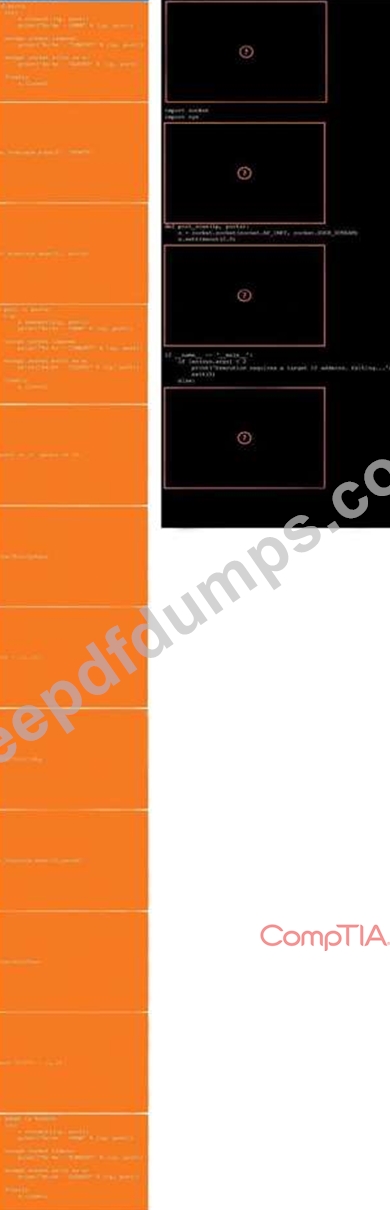
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Premium Bundle
Newest PT0-002 Exam PDF Dumps shared by Actual4test.com for Helping Passing PT0-002 Exam! Actual4test.com now offer the updated PT0-002 exam dumps, the Actual4test.com PT0-002 exam questions have been updated and answers have been corrected get the latest Actual4test.com PT0-002 pdf dumps with Exam Engine here:
(460 Q&As Dumps, 30%OFF Special Discount: Freepdfdumps)






