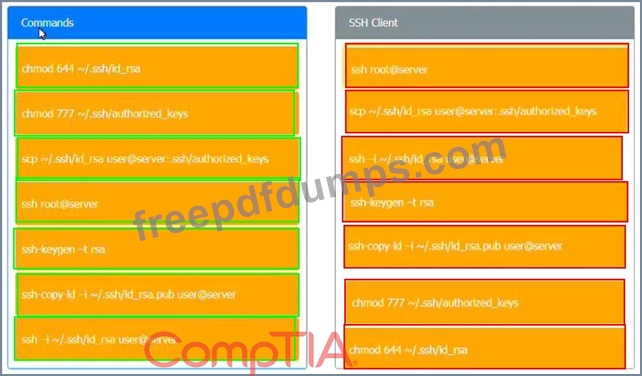
SY0-601 Exam Question 86
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

SY0-601 Exam Question 87
A security modern may have occurred on the desktop PC of an organization's Chief Executive Officer (CEO) A duplicate copy of the CEO's hard drive must be stored securely to ensure appropriate forensic processes and the chain of custody are followed. Which of the following should be performed to accomplish this task?
SY0-601 Exam Question 88
A user contacts the help desk to report the following:
* Two days ago, a pop-up browser window prompted the user for a name and password after connecting to the corporate wireless SSID. This had never happened before, but the user entered the information as requested.
* The user was able to access the Internet but had trouble accessing the department share until the next day.
* The user is now getting notifications from the bank about unauthorized transactions.
Which of the following attack vectors was MOST likely used in this scenario?
* Two days ago, a pop-up browser window prompted the user for a name and password after connecting to the corporate wireless SSID. This had never happened before, but the user entered the information as requested.
* The user was able to access the Internet but had trouble accessing the department share until the next day.
* The user is now getting notifications from the bank about unauthorized transactions.
Which of the following attack vectors was MOST likely used in this scenario?
SY0-601 Exam Question 89
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
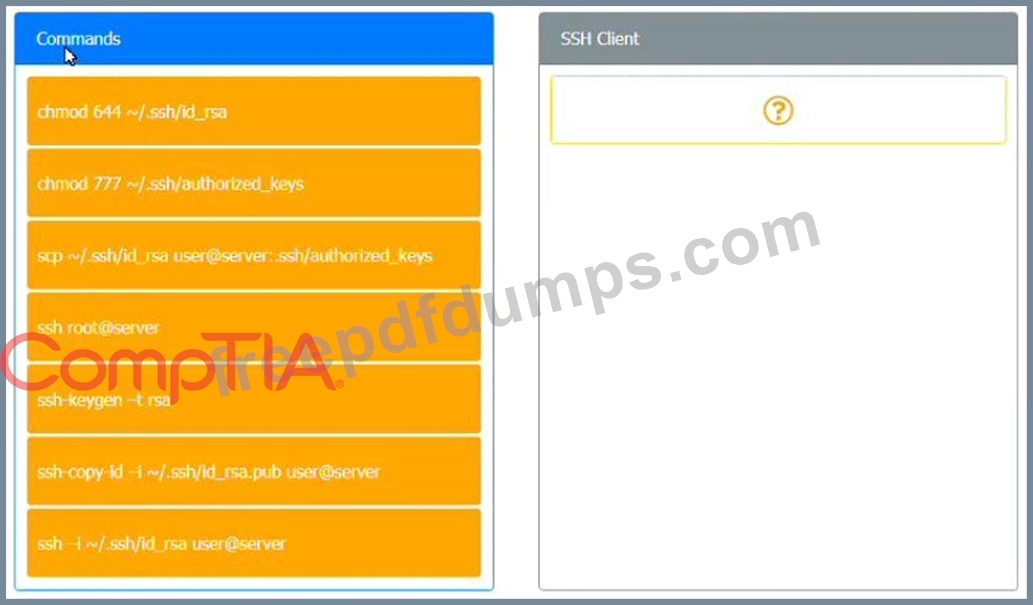
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

SY0-601 Exam Question 90
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
Which of the following describes the method that was used to compromise the laptop?
Which of the following describes the method that was used to compromise the laptop?