SY0-601 Exam Question 116
A security analyst discovers several .jpg photos from a cellular phone during a forensics investigation involving a compromised system. The analyst runs a forensics tool to gather file metadata. Which of the following would be part of the images if all the metadata is still intact?
SY0-601 Exam Question 117
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message:
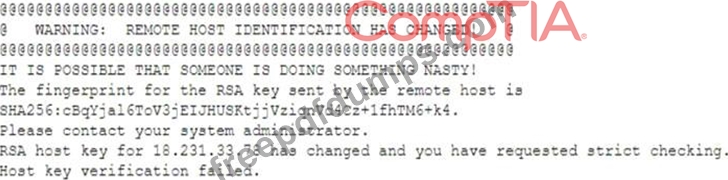
Which of the following network attacks is the researcher MOST likely experiencing?

Which of the following network attacks is the researcher MOST likely experiencing?
SY0-601 Exam Question 118
A security analyst is reviewing the output of a web server log and notices a particular account is attempting to transfer large amounts of money:
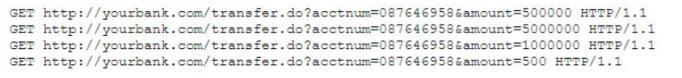
Which of the following types of attack is MOST likely being conducted?

Which of the following types of attack is MOST likely being conducted?
SY0-601 Exam Question 119
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:

Which of the following is the router experiencing?

Which of the following is the router experiencing?
SY0-601 Exam Question 120
A hospital's administration is concerned about a potential loss of patient data that is stored on tablets. A security administrator needs to implement controls to alert the SOC any time the devices are near exits. Which of the following would BEST achieve this objective?

