SY0-601 Exam Question 131
A security analyst is reviewing the following attack log output:
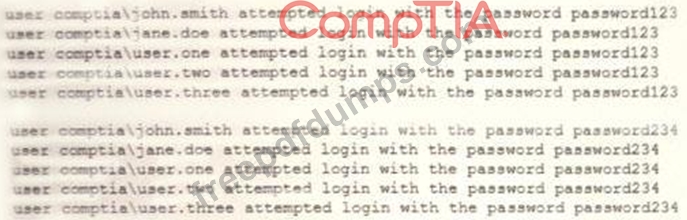
Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?
SY0-601 Exam Question 132
Given the following logs:
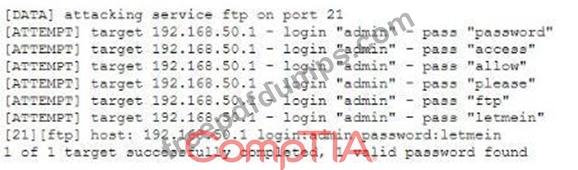
Which of the following BEST describes the type of attack that is occurring?

Which of the following BEST describes the type of attack that is occurring?
SY0-601 Exam Question 133
A large enterprise has moved all Hs data to the cloud behind strong authentication and encryption A sales director recently had a laptop stolen and later, enterprise data was round to have been compromised database.
Which of the following was the MOST likely cause?
Which of the following was the MOST likely cause?
SY0-601 Exam Question 134
A nationwide company is experiencing unauthorized logins at all hours of the day.
The logins appear to originate from countries in which the company has no employees. Which of the following controls.
should the company consider using as part of its IAM strategy? (Select TWO).
The logins appear to originate from countries in which the company has no employees. Which of the following controls.
should the company consider using as part of its IAM strategy? (Select TWO).
SY0-601 Exam Question 135
Several employees return to work the day after attending an industry trade show. That same day, the security manager notices several malware alerts coming from each of the employee's workstations. The security manager investigates but finds no signs of an attack on the perimeter firewall or the NIDS. Which of the following is MOST likely causing the malware alerts?

