SY0-601 Exam Question 246
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
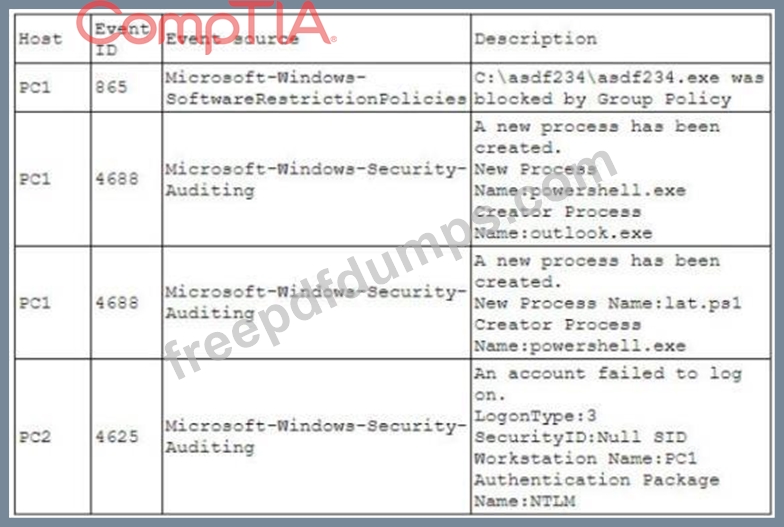
Which of the following describes the method that was used to compromise the laptop?

Which of the following describes the method that was used to compromise the laptop?
SY0-601 Exam Question 247
During an incident response, a security analyst observes the following log entry on the web server:

Which of the following BEST describes the type of attack the analyst is experiencing?

Which of the following BEST describes the type of attack the analyst is experiencing?
SY0-601 Exam Question 248
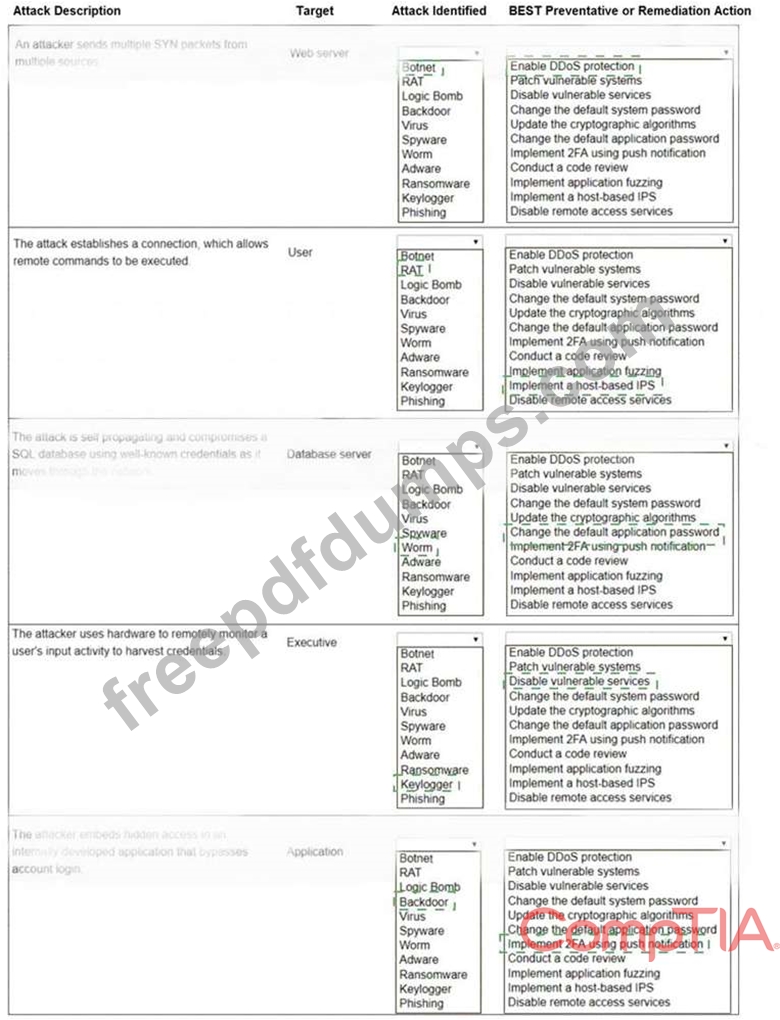
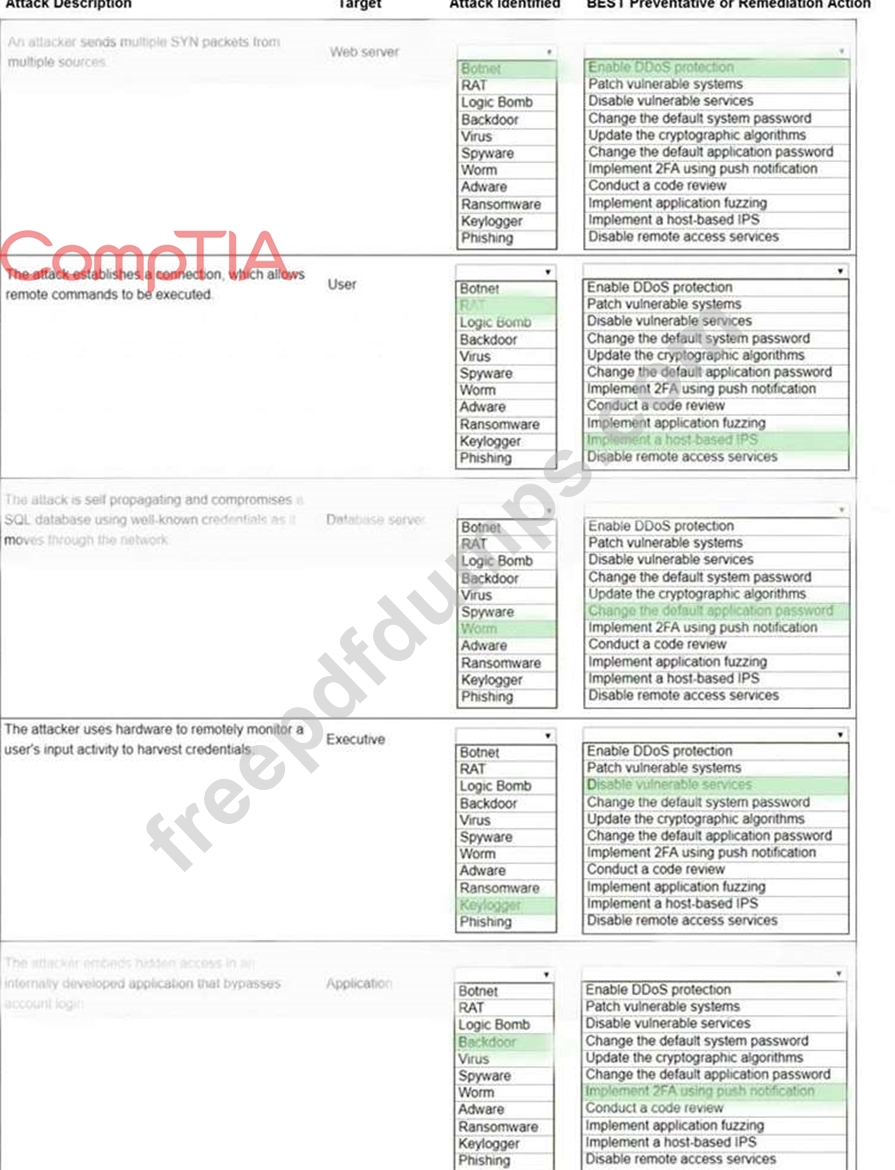
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

SY0-601 Exam Question 249
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output:
Which of the following attacks does the analyst MOST likely see in this packet capture?
Which of the following attacks does the analyst MOST likely see in this packet capture?
SY0-601 Exam Question 250
Which of the following utilize a subset of real data and are MOST likely to be used to assess the features and functions of a system and how it interacts or performs from an end user's perspective against defined test cases? (Select TWO).