SY0-601 Exam Question 296
An organization has implemented a policy requiring the use of conductive metal lockboxes for personal electronic devices outside of a secure research lab. Which of the following did the organization determine to be the GREATEST risk to intellectual property when creating this policy?
SY0-601 Exam Question 297
An organization's RPO for a critical system is two hours. The system is used Monday through Friday, from 9:00 am to 5:00 pm. Currently, the organization performs a full backup every Saturday that takes four hours to complete. Which of the following additional backup implementations would be the BEST way for the analyst to meet the business requirements?
SY0-601 Exam Question 298
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements:
* The devices will be used internationally by staff who travel extensively.
* Occasional personal use is acceptable due to the travel requirements.
* Users must be able to install and configure sanctioned programs and productivity suites.
* The devices must be encrypted
* The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
* The devices will be used internationally by staff who travel extensively.
* Occasional personal use is acceptable due to the travel requirements.
* Users must be able to install and configure sanctioned programs and productivity suites.
* The devices must be encrypted
* The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
SY0-601 Exam Question 299
A security analyst is reviewing logs on a server and observes the following output:
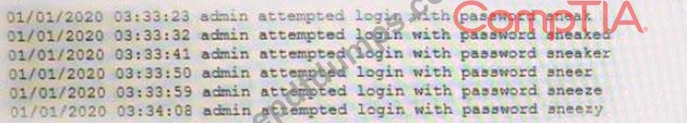
Which of the following is the security analyst observing?

Which of the following is the security analyst observing?
SY0-601 Exam Question 300
An attacker was easily able to log in to a company's security camera by performing a basic online search for a setup guide for that particular camera brand and model Which of the following BEST describes the configurations the attacker exploited?

