SY0-601 Exam Question 56
Which of the following would be BEST for a technician to review to determine the total risk an organization can bear when assessing a "cloud-first" adoption strategy?
SY0-601 Exam Question 57
A forensics investigator is examining a number of unauthorized payments that were reported on the 00mpany's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
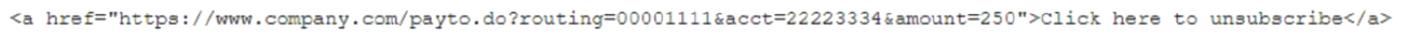
Which of the following will the forensics investigator MOST likely determine has occurred?
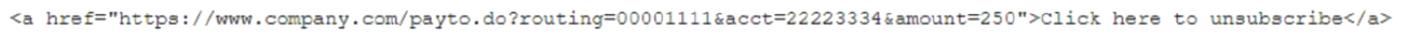
Which of the following will the forensics investigator MOST likely determine has occurred?
SY0-601 Exam Question 58
A recent audit uncovered a key finding regarding the use of a specific encryption standard in a web application that is used to communicate with business customers. Due to the technical limitations of its customers the company is unable to upgrade the encryption standard. Which of the following types of controls should be used to reduce the risk created by this scenario?
SY0-601 Exam Question 59
Accompany deployed a WiFi access point in a public area and wants to harden the configuration to make it more secure. After performing an assessment, an analyst identifies that the access point is
configured to use WPA3, AES, WPS, and RADIUS. Which of the following should the analyst disable to enhance the access point security?
configured to use WPA3, AES, WPS, and RADIUS. Which of the following should the analyst disable to enhance the access point security?
SY0-601 Exam Question 60
Which of the following control sets should a well-written BCP include? (Select THREE)

