SY0-601 Exam Question 121
A security analyst is Investigating a malware incident at a company. The malware Is accessing a command-and-control website at www.comptia.com. All outbound Internet traffic is logged to a syslog server and stored in /logfiles/messages.
Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?
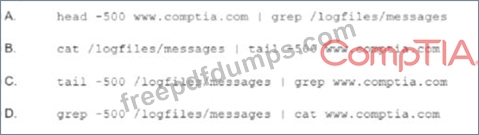
Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?

SY0-601 Exam Question 122
An analyst has determined that a server was not patched and an external actor exfiltrated data on port 139. Which of the following sources should the analyst review to BEST ascertain how the Incident could have been prevented?
SY0-601 Exam Question 123
The chief compliance officer from a bank has approved a background check policy for all new hires. Which of the following is the policy MOST likely protecting against?
SY0-601 Exam Question 124
A recent security assessment revealed that an actor exploited a vulnerable workstation within an organization and has persisted on the network for several months. The organization realizes the need to reassess Its security.
Strategy for mitigating risks within the perimeter Which of the following solutions would BEST support the organization's strategy?
Strategy for mitigating risks within the perimeter Which of the following solutions would BEST support the organization's strategy?
SY0-601 Exam Question 125
A client sent several inquiries to a project manager about the delinquent delivery status of some critical reports. The project manager claimed the reports were previously sent via email, but then quickly generated and backdated the reports before submitting them as plain text within the body of a new email message thread. Which of the following actions MOST likely supports an investigation for fraudulent submission?

