SY0-601 Exam Question 166
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:
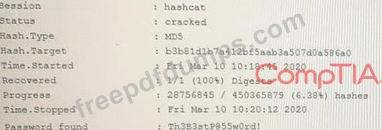
Which of the following BEST describes the type of password attack the attacker is performing?

Which of the following BEST describes the type of password attack the attacker is performing?
SY0-601 Exam Question 167
An incident response technician collected a mobile device during an investigation. Which of the following should the technician do to maintain chain of custody?
SY0-601 Exam Question 168
An incident, which is affecting dozens of systems, involves malware that reaches out to an Internet service for rules and updates. The IP addresses for the Internet host appear to be different in each case. The organization would like to determine a common IoC to support response and recovery actions. Which of the following sources of information would BEST support this solution?
SY0-601 Exam Question 169
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
SY0-601 Exam Question 170
The Chief Executive Officer (CEO) of an organization would like staff members to have the flexibility to work from home anytime during business hours, incident during a pandemic or crisis, However, the CEO is concerned that some staff members may take advantage of the of the flexibility and work from high-risk countries while on holidays work to a third-party organization in another country. The Chief information Officer (CIO) believes the company can implement some basic to mitigate the majority of the risk. Which of the following would be BEST to mitigate CEO's concern? (Select TWO).

