SY0-601 Exam Question 206
An analyst is reviewing logs associated with an attack. The logs indicate an attacker downloaded a malicious file that was quarantined by the AV solution. The attacker utilized a local non-administrative account to restore the malicious file to a new location. The file was then used by another process to execute a payload.
Which of the following attacks did the analyst observe?
Which of the following attacks did the analyst observe?
SY0-601 Exam Question 207
A company is designing the layout of a new datacenter so it will have an optimal environmental temperature Which of the following must be included? (Select TWO)
SY0-601 Exam Question 208
During an incident response, a security analyst observes the following log entry on the web server.
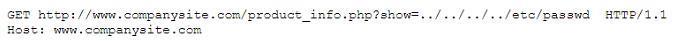
Which of the following BEST describes the type of attack the analyst is experience?
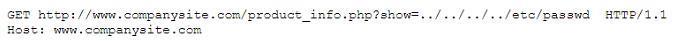
Which of the following BEST describes the type of attack the analyst is experience?
SY0-601 Exam Question 209
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message:
Which of the following network attacks is the researcher MOST likely experiencing?
Which of the following network attacks is the researcher MOST likely experiencing?
SY0-601 Exam Question 210
The Chief Information Security Officer wants to pilot a new adaptive, user-based authentication method. The concept Includes granting logical access based on physical location and proximity. Which of the following Is the BEST solution for the pilot?

