SY0-601 Exam Question 306
A security analyst was deploying a new website and found a connection attempting to authenticate on the site's portal. While Investigating The incident, the analyst identified the following Input in the username field:
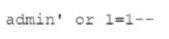
Which of the following BEST explains this type of attack?
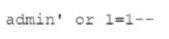
Which of the following BEST explains this type of attack?
SY0-601 Exam Question 307
Which of the following job roles would sponsor data quality and data entry initiatives that ensure business and regulatory requirements are met?
SY0-601 Exam Question 308
An organization's Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained. Which of the following roles would MOST likely include these responsibilities?
SY0-601 Exam Question 309
A security analyst receives the configuration of a current VPN profile and notices the authentication is only applied to the IP datagram portion of the packet. Which of the following should the analyst implement to authenticate the entire packet?
SY0-601 Exam Question 310
An enterprise needs to keep cryptographic keys in a safe manner. Which of the following network appliances can achieve this goal?

