SY0-601 Exam Question 381
Which of the following is MOST likely to contain ranked and ordered information on the likelihood and potential impact of catastrophic events that may affect business processes and systems, while also highlighting the residual risks that need to be managed after mitigating controls have been implemented?
SY0-601 Exam Question 382
An IT security manager requests a report on company information that is publicly available. The manager's concern is that malicious actors will be able to access the data without engaging in active reconnaissance.
Which of the following is the MOST efficient approach to perform the analysis?
Which of the following is the MOST efficient approach to perform the analysis?
SY0-601 Exam Question 383
Which of the following authentication methods sends out a unique password to be used within a specific number of seconds?
SY0-601 Exam Question 384
While reviewing the wireless router, a systems administrator of a small business determines someone is spoofing the MAC address of an authorized device.
Given the table below:
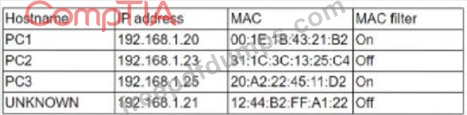
Which of the following should be the administrator's NEXT step to detect if there is a rague system without impacting availability?
Given the table below:

Which of the following should be the administrator's NEXT step to detect if there is a rague system without impacting availability?
SY0-601 Exam Question 385
A security analyst discovers that a company username and password database was posted on an internet forum.
The username and passwords are stored in plan text. Which of the following would mitigate the damage done by this type of data exfiltration in the future?
The username and passwords are stored in plan text. Which of the following would mitigate the damage done by this type of data exfiltration in the future?

