SY0-601 Exam Question 331
A backdoor was detected on the containerized application environment. The investigation detected that a zero-day vulnerability was introduced when the latest container image version was downloaded from a public registry. Which of the following is the BEST solution to prevent this type of incident from occurring again?
SY0-601 Exam Question 332
Security analysts notice a server login from a user who has been on vacation for two weeks The analysts confirm that the user did not log in to the system while on vacation After reviewing packet capture logs, the analysts notice the following:
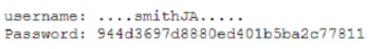
Which of the following occurred?

Which of the following occurred?
SY0-601 Exam Question 333
A systems analyst is responsible for generating a new digital forensics chain-of-custody form. Which of the following should the analyst include in this documentation? (Select TWO).
SY0-601 Exam Question 334
A security analyst is looking for a solution to help communicate to the leadership team the seventy levels of the organization's vulnerabilities. Which of the following would BEST meet this need?
SY0-601 Exam Question 335
Which of the following processes will eliminate data using a method that will allow the storage device to be reused after the process is complete?

