SY0-601 Exam Question 376
n attack relies on an end user visiting a website the end user would typically visit; however, the site is compromised and uses vulnerabilities in the end user's browser to deploy malicious software. Which of the following types of attack does this describe?
SY0-601 Exam Question 377
Which of the following is a risk that is specifically associated with hosting applications in the public cloud?
SY0-601 Exam Question 378
A bank detects fraudulent activity on user's account. The user confirms transactions completed yesterday on the bank's website at https:/Awww.company.com. A security analyst then examines the user's Internet usage logs and observes the following output:
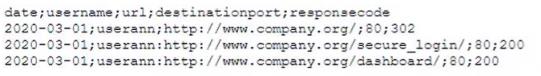
Which of the following has MOST likely occurred?

Which of the following has MOST likely occurred?
SY0-601 Exam Question 379
The Chief information Security Officer wants to prevent exfilitration of sensitive information from employee cell phones when using public USB power charging stations. Which of the following would be the Best solution to implement?
SY0-601 Exam Question 380
An ofgantzation has decided to purchase an insurance policy because a risk assessment determined that the cost to remediate the risk is greater than the five-year cost of the insurance policy. The organization is enabling risk

