SY0-601 Exam Question 141
A security administrator wants to implement a program that tests a user's ability to recognize attacks over the organization's email system Which of the following would be BEST suited for this task?
SY0-601 Exam Question 142
Which of the technologies is used to actively monitor for specific file types being transmitted on the network?
SY0-601 Exam Question 143
Employees at a company are receiving unsolicited text messages on their corporate cell phones. The unsolicited text messages contain a password reset Link. Which of the attacks is being used to target the company?
SY0-601 Exam Question 144
A security analyst was deploying a new website and found a connection attempting to authenticate on the site's portal. While Investigating The incident, the analyst identified the following Input in the username field:
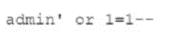
Which of the following BEST explains this type of attack?
Which of the following BEST explains this type of attack?
SY0-601 Exam Question 145
Which of the following would provide guidelines on how to label new network devices as part of the initial configuration?

