CS0-002 Exam Question 1
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company The text of one of the emails is shown below:
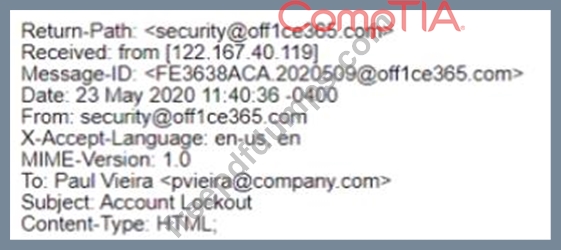
Office 365 User.
It looks like you account has been locked out Please click this <a href=Tittp7/accountfix-office356 com/login php">link</a> and follow the pfompts to restore access Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?

Office 365 User.
It looks like you account has been locked out Please click this <a href=Tittp7/accountfix-office356 com/login php">link</a> and follow the pfompts to restore access Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?
CS0-002 Exam Question 2
The Chief Information Officer (CIO) for a large manufacturing organization has noticed a significant number of unknown devices with possible malware infections are on the organization's corporate network.
Which of the following would work BEST to prevent the issue?
Which of the following would work BEST to prevent the issue?
CS0-002 Exam Question 3
A cybersecurity analyst needs to determine whether a large file named access log from a web server contains the following loC:
../../../../bin/bash
Which of the following commands can be used to determine if the string is present in the log?
../../../../bin/bash
Which of the following commands can be used to determine if the string is present in the log?
CS0-002 Exam Question 4
A team of security analysis has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team's NEXT step during the detection phase of this response process?
CS0-002 Exam Question 5
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities:

Which of the following is the MOST likely solution to the listed vulnerability?

Which of the following is the MOST likely solution to the listed vulnerability?

