CS0-002 Exam Question 136
A security analyst discovers accounts in sensitive SaaS-based systems are not being removed in a timely manner when an employee leaves the organization To BEST resolve the issue, the organization should implement
CS0-002 Exam Question 137
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to devices within the ICS environment without compromising security.
To provide the MOST secure access model in this scenario, the jumpbox should be .
To provide the MOST secure access model in this scenario, the jumpbox should be .
CS0-002 Exam Question 138
D18912E1457D5D1DDCBD40AB3BF70D5D
A security analyst scanned an internal company subnet and discovered a host with the following Nmap output.
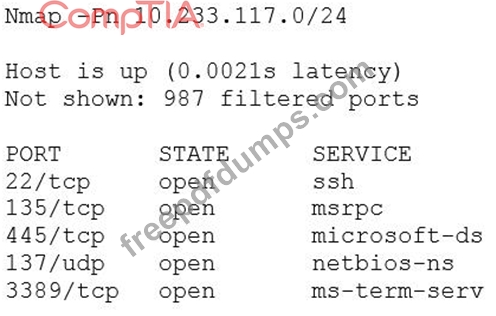
Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
A security analyst scanned an internal company subnet and discovered a host with the following Nmap output.

Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
CS0-002 Exam Question 139
A financial organization has offices located globally. Per the organization's policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's dat a. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
CS0-002 Exam Question 140
A team of network security analysts is examining network traffic to determine if sensitive data was exfitrated Upon further investigation, the analysts believe confidential data was compromised. Which of me following capattlnes would BEST defend against tnts type of sensitive data eifiitraUon?

