CS0-003 Exam Question 1
The analyst reviews the following endpoint log entry:
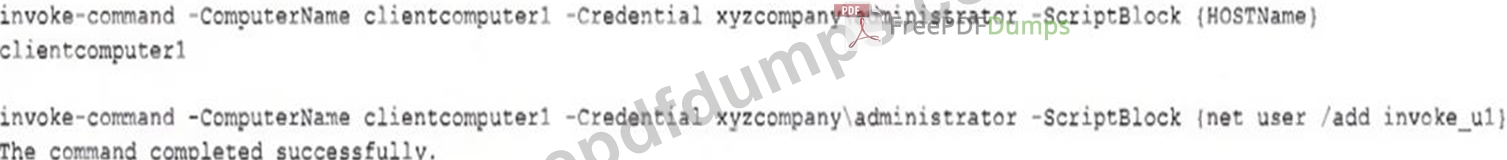
Which of the following has occurred?

Which of the following has occurred?
CS0-003 Exam Question 2
A security analyst has found the following suspicious DNS traffic while analyzing a packet capture:
* DNS traffic while a tunneling session is active.
* The mean time between queries is less than one second.
* The average query length exceeds 100 characters.
Which of the following attacks most likely occurred?
* DNS traffic while a tunneling session is active.
* The mean time between queries is less than one second.
* The average query length exceeds 100 characters.
Which of the following attacks most likely occurred?
CS0-003 Exam Question 3
A systems administrator is reviewing after-hours traffic flows from data-center servers and sees regular outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?
CS0-003 Exam Question 4
A systems administrator notices unfamiliar directory names on a production server. The administrator reviews the directory listings and files, and then concludes the server has been compromised. Which of the following steps should the administrator take next?
CS0-003 Exam Question 5
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.
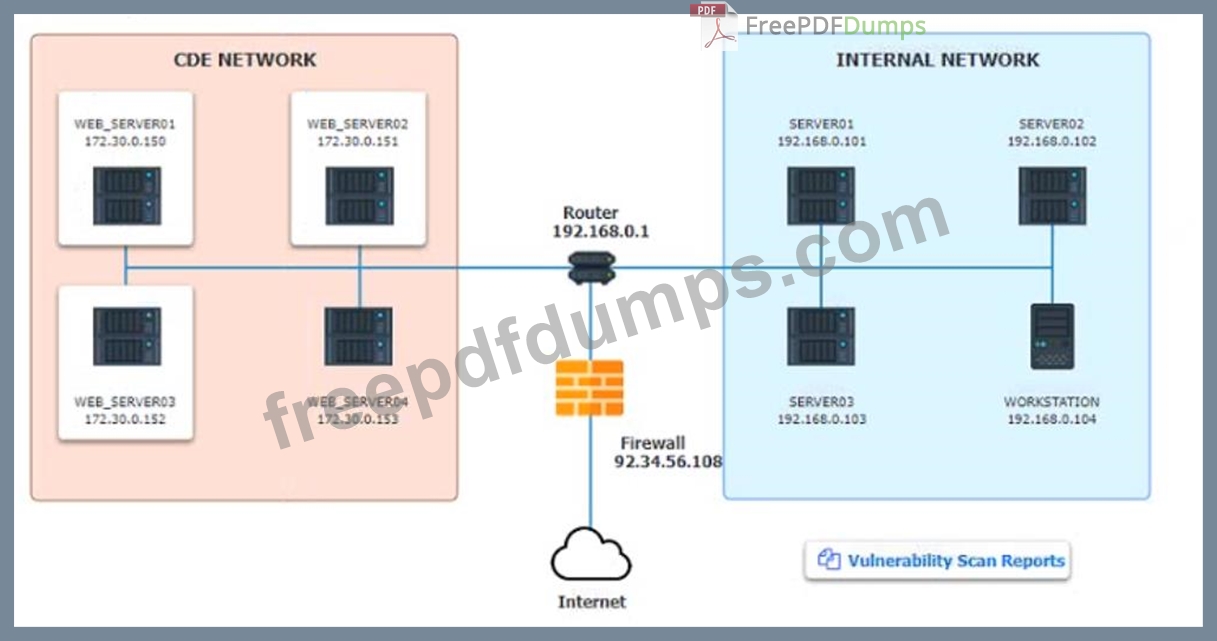
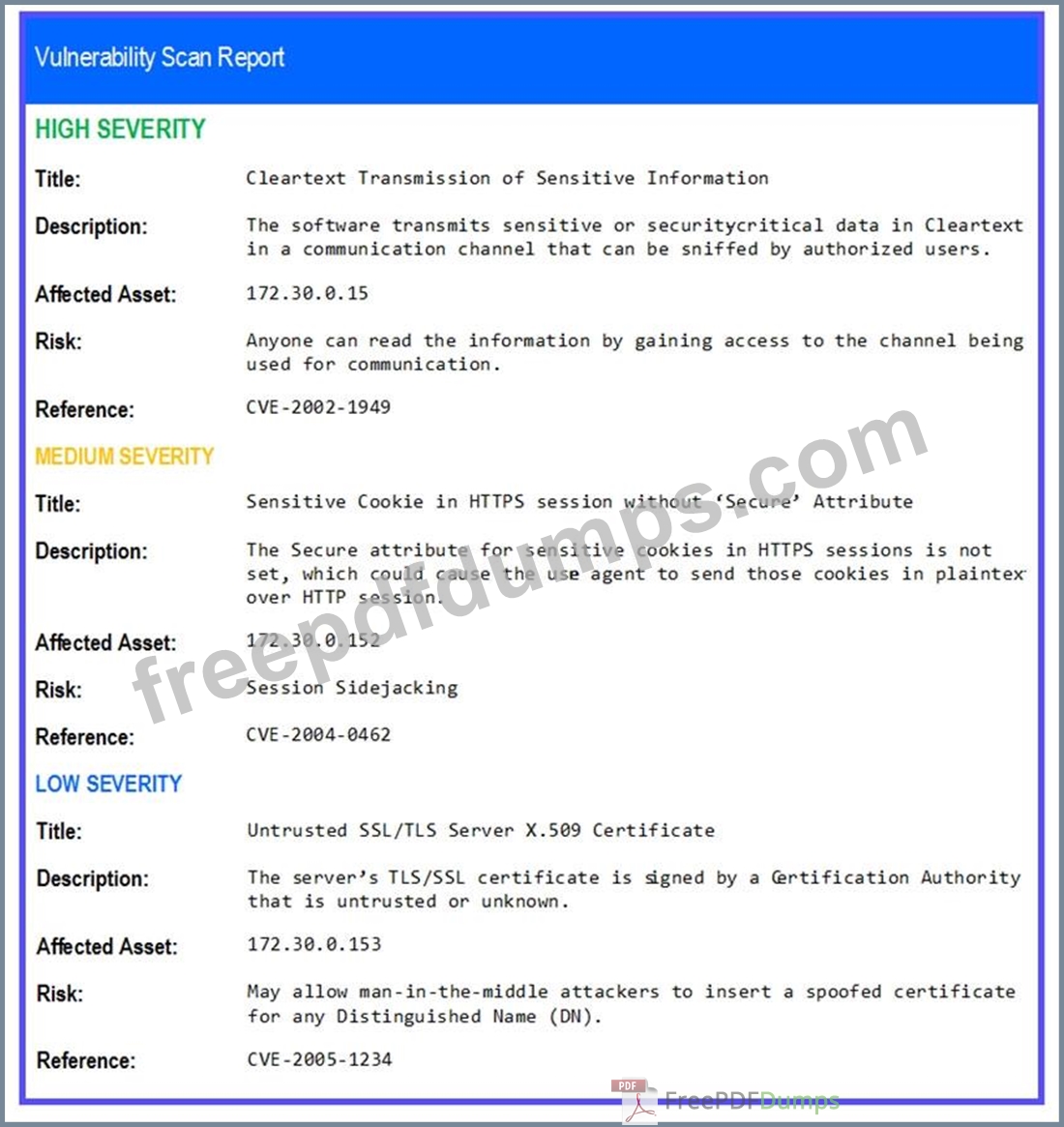
STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.
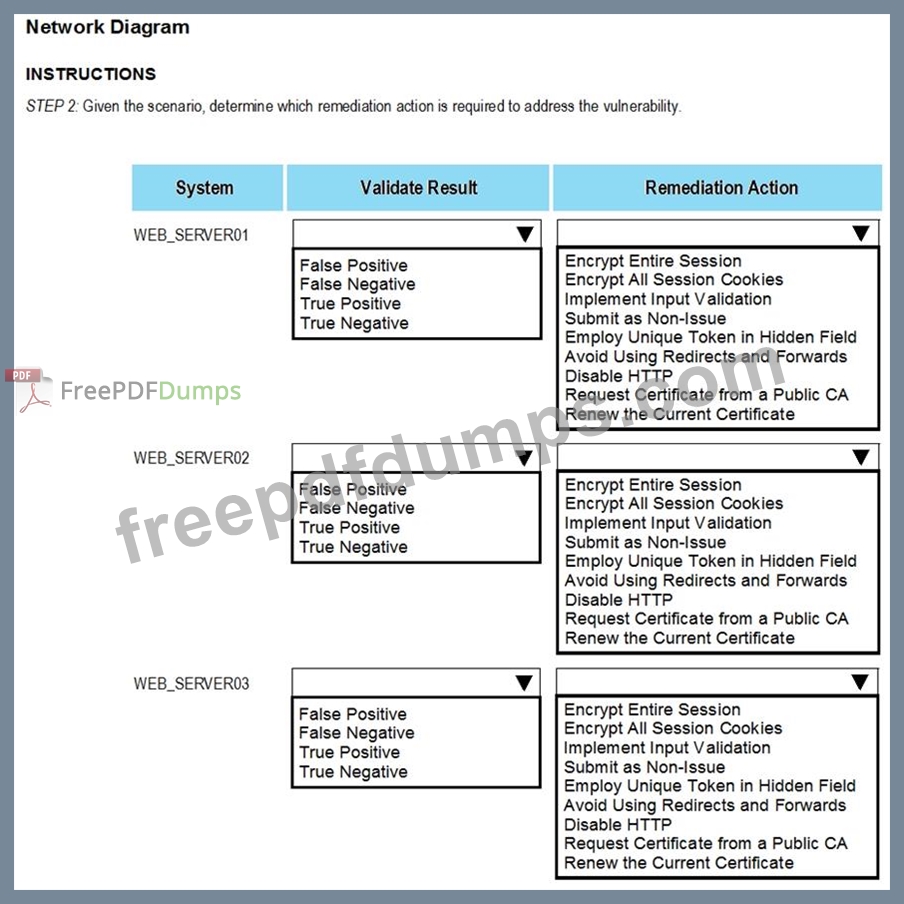
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.


STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.



