312-39 Exam Question 1
Which of the following data source will a SOC Analyst use to monitor connections to the insecure ports?
312-39 Exam Question 2
Identify the attack when an attacker by several trial and error can read the contents of a password file present in the restricted etc folder just by manipulating the URL in the browser as shown:
http://www.terabytes.com/process.php./../../../../etc/passwd
http://www.terabytes.com/process.php./../../../../etc/passwd
312-39 Exam Question 3
Which of the following attack can be eradicated by converting all non-alphanumeric characters to HTML character entities before displaying the user input in search engines and forums?
312-39 Exam Question 4
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.
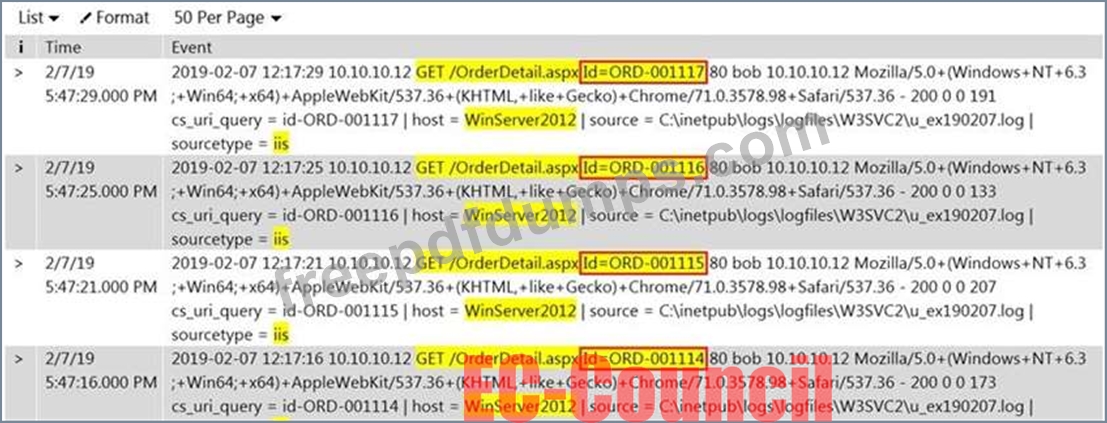
What does this event log indicate?

What does this event log indicate?
312-39 Exam Question 5
Identify the password cracking attempt involving a precomputed dictionary of plaintext passwords and their corresponding hash values to crack the password.

