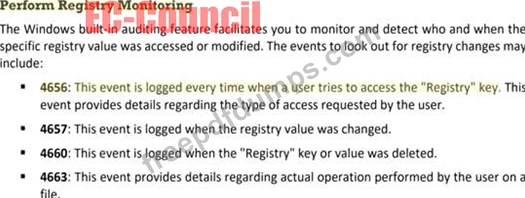
312-39 Exam Question 21
Which of the following Windows event is logged every time when a user tries to access the "Registry" key?
312-39 Exam Question 22
Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
312-39 Exam Question 23
Which of the following threat intelligence is used by a SIEM for supplying the analysts with context and
"situational awareness" by using threat actor TTPs, malware campaigns, tools used by threat actors.
1.Strategic threat intelligence
2.Tactical threat intelligence
3.Operational threat intelligence
4.Technical threat intelligence
"situational awareness" by using threat actor TTPs, malware campaigns, tools used by threat actors.
1.Strategic threat intelligence
2.Tactical threat intelligence
3.Operational threat intelligence
4.Technical threat intelligence
312-39 Exam Question 24
Which of the following steps of incident handling and response process focus on limiting the scope and extent of an incident?
312-39 Exam Question 25
Which of the following attack inundates DHCP servers with fake DHCP requests to exhaust all available IP addresses?