312-49v10 Exam Question 166
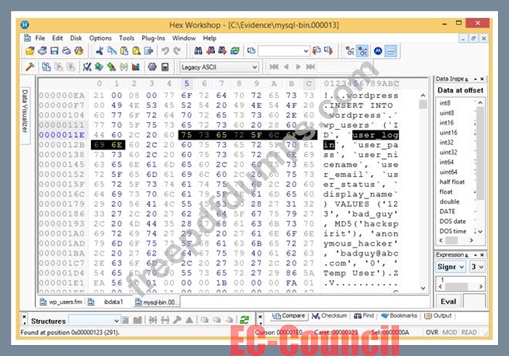
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?

312-49v10 Exam Question 167
You have been asked to investigate after a user has reported a threatening e-mail they have received from an external source. Which of the following are you most interested in when trying to trace the source of the message?
312-49v10 Exam Question 168
When a file is deleted by Windows Explorer or through the MS-DOS delete command, the operating system inserts _______________ in the first letter position of the filename in the FAT database.
312-49v10 Exam Question 169
If the partition size is 4 GB, each cluster will be 32 K. Even if a file needs only 10 K, the entire 32 K will be allocated, resulting in 22 K of ________.
312-49v10 Exam Question 170
Which of the following tool can the investigator use to analyze the network to detect Trojan activities?

